
Leveraging AI/ML to improve MDR efficiency and reduce false positives
Key Findings from the 2023 MDR...

Safeguarding Your Cloud Resources: Defending Against Muddled Libra Threats
In response to the evolving tactics of threat actors like Muddled Libra, organizations must prioritize robust cybersecurity measures to safeguard their cloud resources

Beware the Lazy Koala: Unveiling the Threat of Basic Malware in Government Organizations
Targeting government organizations across several countries, Lazy Koala's tactics underscore the importance of user education, layered security measures, and continuous monitoring in safeguarding against cyber threats

New Year Cyber Threats Unveiled: Remcos RAT Targets Celebratory Spirit in Deceptive Campaign
A Sophisticated New Year Cyber Threat Exploits Celebratory Spirit, as Remcos RAT Orchestrates Multi-Stage Malware Campaign Through Deceptive Spam Emails
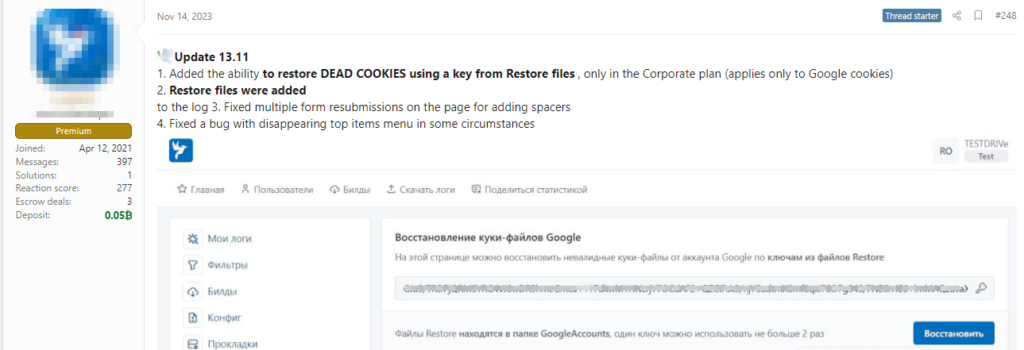
Malicious Exploits Threaten Persistent Access to Google Accounts
Cybercriminals Exploit OAuth 2.0 Vulnerabilities in Malware-as-a-Service, Gaining Persistent Access to Google Accounts Despite Password Resets
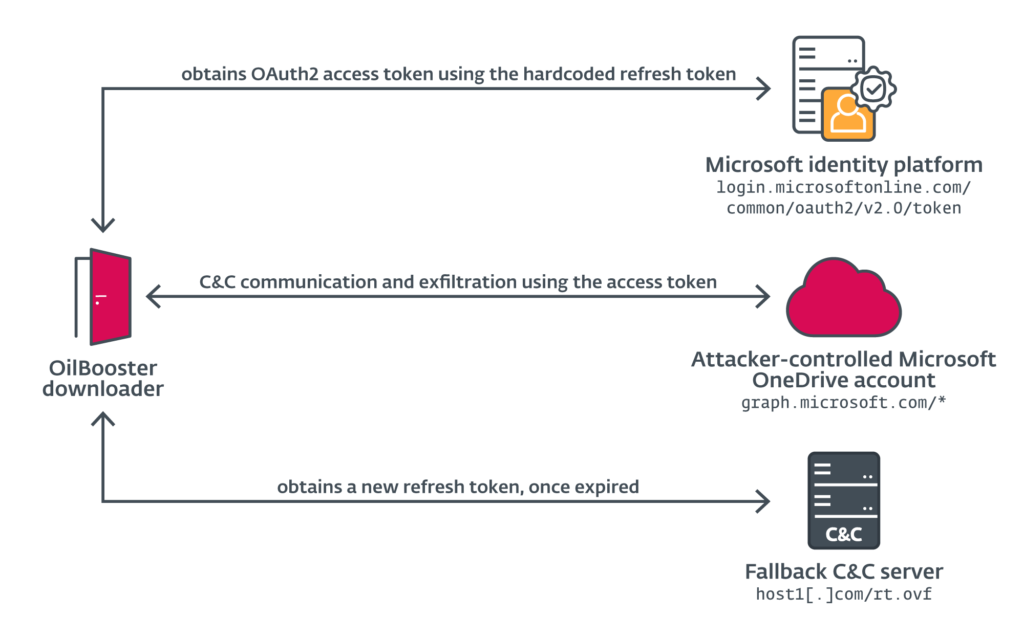
OilRig’s Stealthy Tactics: A Deep Dive into the 2022 Cybersecurity Report by ESET
The intricate world of cybersecurity tactics as we unravel OilRig's sophisticated methods in the deployment of malicious loaders. Delve into the report by ESET, discovering the group's use of Microsoft cloud services, targeted sectors, and shared communication accounts. Stay informed to bolster your defense against evolving cyber threats in 2023

TA4557: The Sinister Evolution of Job Recruitment Deception
Uncover the sinister tactics of TA4557, a cyber threat group weaving a web of deception in the realm of job recruitment. Dive into their evolved methods, from benign emails to intricate malware deployment, revealing the need for heightened vigilance in the face of sophisticated cyber threats
Unveiling the Enigma: The Sinister Dance of PlugX Malware in the Shadows of Cyber Espionage
Explore the shadowy world of cyber threats with PlugX malware, a sophisticated force adept at espionage and evasion. Uncover its insidious techniques, from process masquerading to keylogging, revealing the evolving challenges in cybersecurity defense
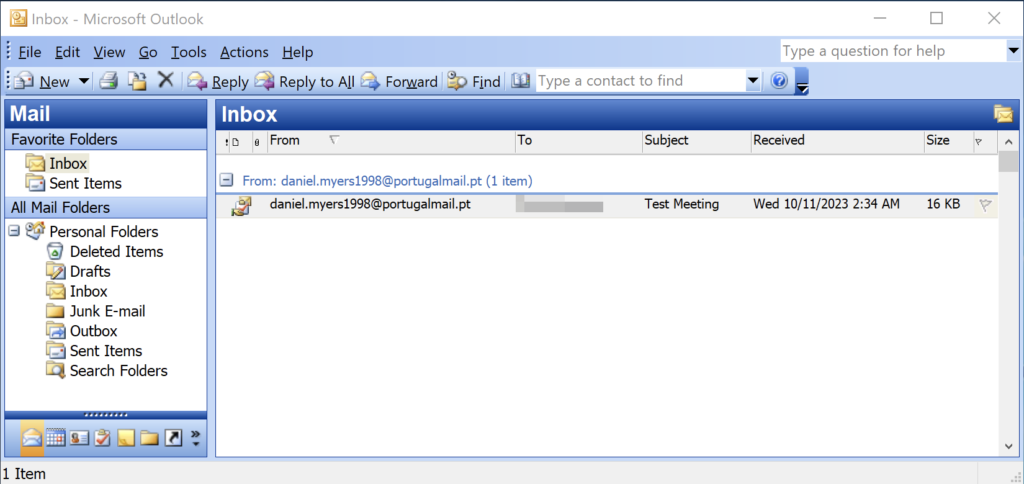
Fighting Ursa’s Covert Campaign: A Threat to Digital Security
In the wake of Unit 42 researchers exposing Fighting Ursa's covert campaign, organizations and governments are urged to take proactive measures to protect their systems from cyber espionage attacks utilizing Microsoft Outlook vulnerabilities