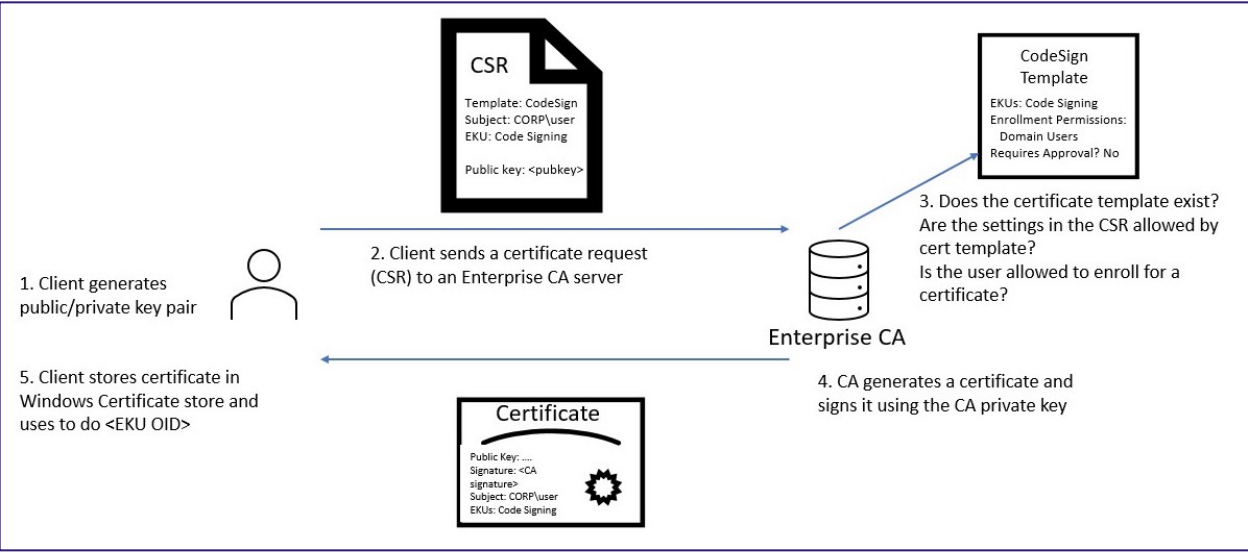
Microsoft’s Active Directory Certificate Services (AD CS), a PKI implementation in Active Directory environments, has been found to contain critical vulnerabilities that can enable attackers to gain long-term persistence in compromised networks. Security researchers have identified several attack vectors that exploit AD CS components, including:
Vulnerabilities
Certificate Theft: Extrusion of user and machine certificates, including private keys, for impersonation purposes.
Malicious Certificate Enrollments: Low-privileged users requesting certificates with elevated privileges, leading to domain escalation.
Certificate Template Misconfigurations: Allowing requesters to specify Subject Alternative Names (SANs), potentially granting access to any user, including administrators.
EDITF_ATTRIBUTESUBJECTALTNAME2 Flag: Enables arbitrary SAN specification in certificate requests, increasing risk of privilege escalation.
CA Private Key Theft: Compromising a Certificate Authority (CA) private key for unrestricted certificate forgery.
Exploitation Scenarios
One of the most severe vulnerabilities involves misconfigured certificate templates. An attacker can exploit a template that allows SANs and Extended Key Usage (EKU) for domain authentication to request a certificate for any user, effectively granting domain admin privileges.
Mitigation Strategies
To mitigate these risks, organizations should:
- Treat CA servers as critical assets, applying strict security measures.
- Audit and harden certificate template settings, particularly those related to SANs and enrollment permissions.
- Disable the EDITF_ATTRIBUTESUBJECTALTNAME2 flag on CAs.
- Implement stringent user mappings for certificate authentication.
- Protect CA private keys using hardware security modules (HSMs).
- Monitor certificate enrollments, authentications, and template modifications.
Importance of Understanding AD CS
While AD CS is not inherently insecure, its complexity and often misunderstood nature make it susceptible to misconfigurations. Failure to understand the security implications of various AD CS settings can leave networks vulnerable to sophisticated persistence techniques.
Conclusion
As PKI becomes increasingly prevalent for authentication and encryption, organizations must comprehend and properly secure AD CS deployments. Neglecting this can lead to severe consequences, including persistent attacker access that is challenging to detect and remediate. By adopting robust mitigation strategies and implementing best practices, organizations can strengthen their security posture against these vulnerabilities.