A new Android banking trojan, dubbed Crocodilus, has been discovered targeting users primarily in Spain and Turkey. This malware isn’t just another clone; it’s a fully-fledged threat employing modern techniques from the outset.
Key capabilities and technical details
- Device Takeover (DTO): Crocodilus1 is designed to facilitate full device takeover to conduct fraudulent transactions.
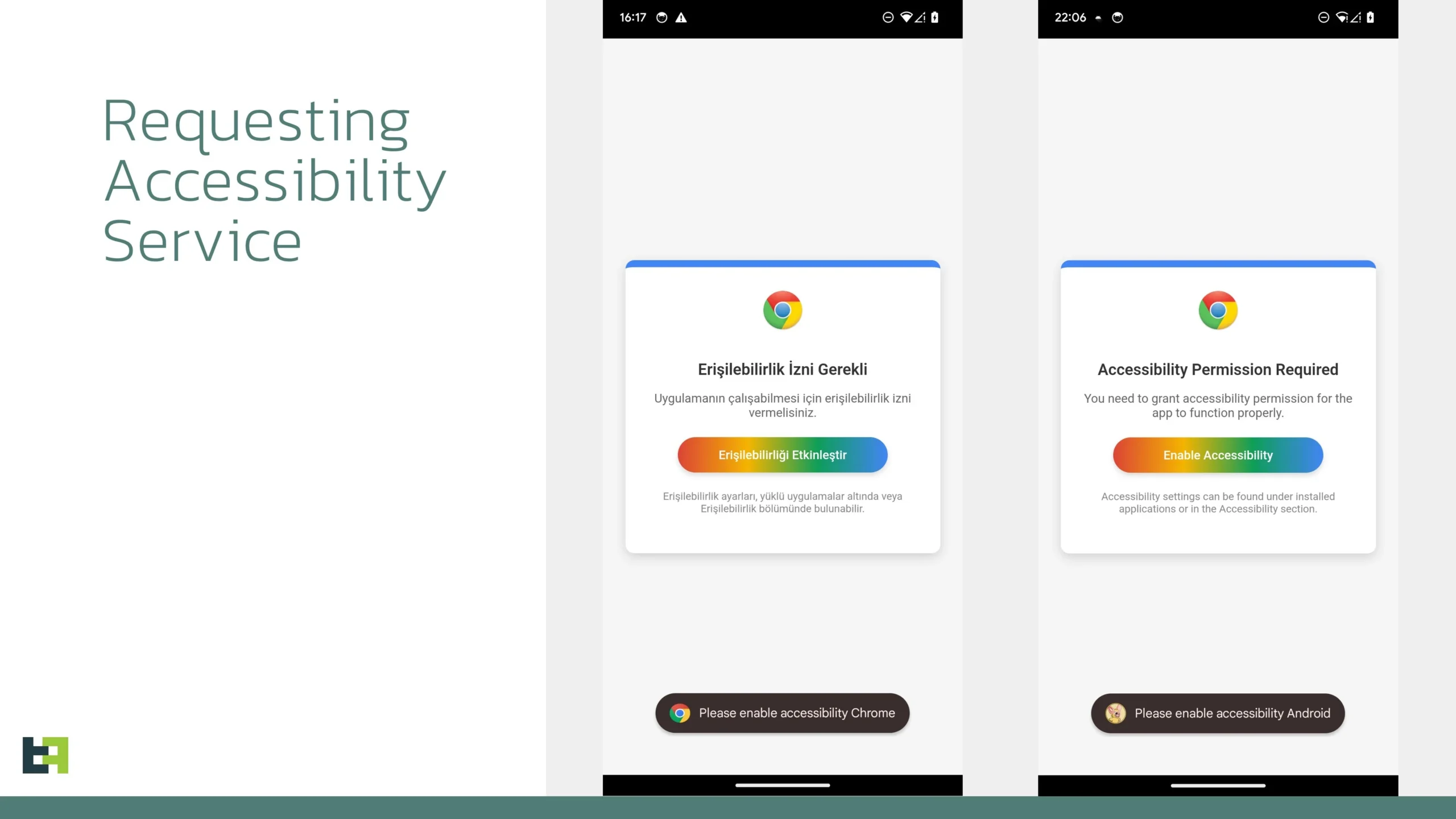
- Distribution: the analyzed samples masquerade as a legitimate Google Chrome app (package name: “quizzical.washbowl.calamity”), acting as a dropper that bypasses Android 13+ restrictions.
- Accessibility Service Abuse: upon installation, Crocodilus requests access to Android’s Accessibility Services. This is a critical step, as it allows the malware to monitor and control the device.
- Command and Control (C2) Communication: once accessibility permissions are granted, the malware establishes communication with a remote server to receive instructions, including a list of targeted financial applications and HTML overlays for credential theft. Analysis of debug messages suggests the author is Turkish-speaking.
- Overlay Attacks: Crocodilus uses HTML overlays to steal credentials from targeted financial applications.
- Cryptocurrency Wallet Targeting: Crocodilus employs a social engineering tactic targeting cryptocurrency wallets. Instead of a fake login page, it displays an alert urging users to back up their seed phrases within 12 hours, tricking them into revealing their seed phrases via the Accessibility Services.
- Continuous Monitoring: Crocodilus runs continuously, monitoring app launches and displaying overlays to intercept credentials. It captures all elements displayed on the screen.
- Google Authenticator Capture: the malware can trigger a screen capture of the contents of the Google Authenticator application, enabling it to bypass 2FA.
- Black Screen Overlay: to conceal malicious activity, Crocodilus can display a black screen overlay and mute sounds.
Notable features
- Application Launching
- Self-Removal
- Push Notifications
- SMS capabilities (sending, retrieving, contact list access)
- Installed Application Listing
- Device Admin Privilege Requests
- Black Overlay Activation
- C2 Setting Updates
- Sound Control
- Keylogging (Enable/Disable)
- SMS Manager Control
Threat level assessment
ThreatFabric assesses Crocodilus as a significant escalation in the Android malware landscape due to its advanced DTO capabilities, remote control features, and early deployment of black overlay attacks. Its maturity level is uncommon for newly discovered threats.
This discovery coincides with reports of a Grandoreiro banking trojan campaign targeting Windows users in Mexico, Argentina, and Spain, using tax-themed phishing lures.
IOC
- Package name: quizzical.washbowl.calamity
This information should provide a solid base for further investigation and defensive measures against this emerging threat.