Endpoint Detection and Response (EDR) solutions are essential for modern cybersecurity defenses. However, research has revealed a vulnerability in Windows MiniFilter drivers that can be exploited to prevent EDR drivers from loading, effectively blinding telemetry and compromising endpoint security.
Exploiting the MiniFilter Architecture
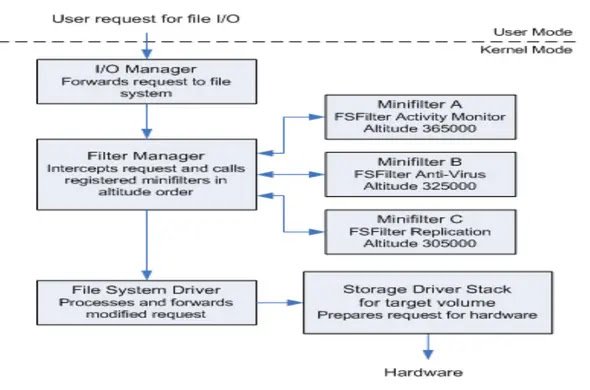
The Filter Manager in Windows manages multiple MiniFilter drivers. Each MiniFilter has an “Altitude” value that determines its load order. By exploiting this architecture, attackers can create a MiniFilter that loads before the EDR driver and allocates the EDR driver’s Altitude to itself. This prevents the EDR driver from registering with the Filter Manager, blocking its ability to load.
Microsoft’s Mitigation Attempts
Microsoft has implemented mitigations to prevent this vulnerability. When researchers attempted to modify the altitude of the Sysmon driver to match that of the Microsoft Defender for Endpoint (MDE) driver, a warning was raised and the regedit process was terminated.
However, researchers discovered that this mitigation could be bypassed using different registry types, such as REG_MULTI_SZ. Microsoft has since patched this vulnerability.
Additional Mitigations
MiniFilter now supports dynamic Altitude values that change upon each load, making it more difficult for attackers to assign specific Altitudes to other drivers. Additionally, researchers demonstrated that altering the registry settings for the Sysmon driver can allow it to load before WdFilter, preventing the exploitation of this vulnerability.
Vendor Impact
While the vulnerability has been mitigated in Microsoft Defender for Endpoint, it still affects certain EDR vendors. SOC teams should monitor registry changes related to Altitude for all MiniFilters and promptly address any suspicious activity.
Conclusion
The Windows MiniFilter vulnerability is a serious threat to EDR security, as it allows attackers to disable telemetry and evade detection. Organizations should ensure that their EDR solutions are updated with the latest patches and implement additional mitigations, such as monitoring registry changes, to protect against this attack vector. By staying vigilant and adopting proactive cybersecurity measures, SOC teams can strengthen their defenses against evolving threats.
Windows MiniFilter vulnerability: a threat to EDR security
dark6
18 September 2024
Read Time:1 Minute, 36 Second