A new wave of cyber threats has emerged, targeting WordPress websites with a sophisticated credit card skimmer that operates through database injections. This malware, which stealthily embeds itself within the WordPress database, specifically targets checkout pages to capture sensitive payment information without raising alarms.
How the malware operates
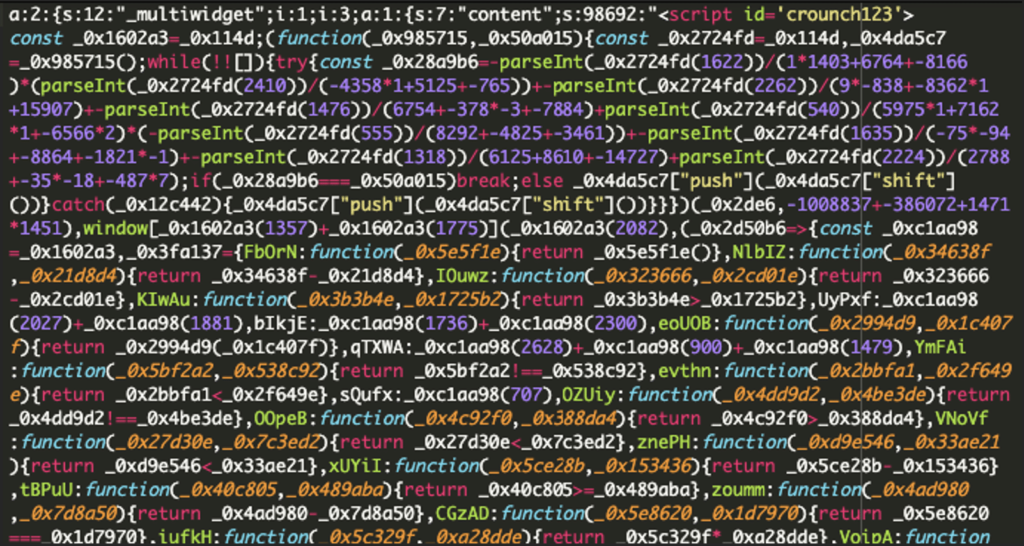
The malicious code is cleverly hidden in the wp_options table of the WordPress database, particularly within the row where the option name is widget_block. This technique allows it to evade detection by conventional file-scanning tools, as it does not reside in theme files or plugins. Instead, it lurks quietly in the database, waiting for the opportune moment to strike during the checkout process.
Upon activation—triggered when a user navigates to a page containing “checkout”—the malware can either hijack existing payment fields or inject a counterfeit payment form that mimics trusted processors like Stripe. This form collects critical information such as credit card numbers, expiration dates, and CVV codes in real-time, ensuring that users unknowingly provide their details directly to the attackers.
Data exfiltration techniques
To obfuscate and securely transmit stolen data, the malware employs Base64 encoding combined with AES-CBC encryption. This dual-layered approach disguises the data during transit, complicating any attempts at analysis. The encoded information is then sent to remote servers controlled by the attackers using the navigator.sendBeacon function, which allows for silent data exfiltration without disrupting the user experience.
Current threat landscape
As of now, two websites have been confirmed as infected with this malware. The malicious domains associated with this threat include valhafather[.]xyz and fqbe23[.]xyz, both of which are currently on blocklists due to their involvement in these attacks. The detection of this malware is facilitated by Sucuri’s SiteCheck tool, which identifies suspicious scripts and obfuscated patterns indicative of such threats.
Mitigation strategies
To protect against this evolving threat landscape, website administrators should take proactive measures:
- Regular updates: keep all software up-to-date to close vulnerabilities that attackers exploit.
- Admin account management: implement strong passwords and two-factor authentication for admin accounts.
- File integrity monitoring: set up systems to detect unauthorized changes in website files.
- Web Application Firewall (WAF): deploying a WAF can effectively block malicious traffic before it reaches your server.
By embedding themselves within databases and targeting critical payment processes, they pose a significant risk to both website owners and consumers alike. Vigilance and robust security practices are essential to combat these stealthy threats and safeguard sensitive information from falling into the wrong hands.