In the ever-evolving cybersecurity landscape, state-sponsored threat actors continue to pose significant risks to organizations worldwide. Among them is UNC1860, an Iranian-based cyber espionage group recently exposed by Mandiant.
Sophisticated Tactics and Tools
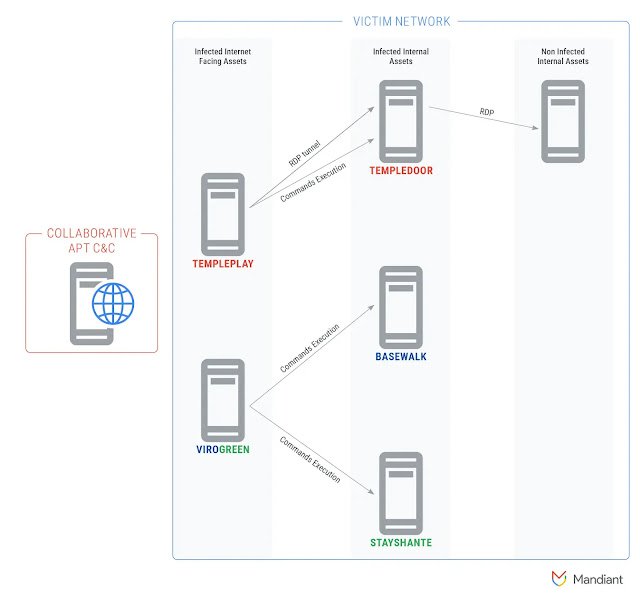
UNC1860 employs a sophisticated suite of tools and techniques to infiltrate high-value targets in the Middle East, including governments and telecommunications sectors. Their customized malware controllers, TEMPLEPLAY and VIROGREEN, provide remote access and control over compromised systems, facilitating covert operations.
One notable aspect of UNC1860’s toolkit is the repurposing of drivers from Iranian antivirus software. This demonstrates their exceptional technical proficiency in manipulating Windows kernels, allowing them to bypass detection and maintain long-term access to compromised networks.
Initial Access and Lateral Movement
UNC1860 specializes in gaining initial access to target networks through passive utilities. These tools evade traditional antivirus detection and enable the group to establish a foothold within victim systems. Once established, they utilize lateral movement techniques to spread across the network, compromising sensitive data and disrupting operations.
Links to Other Iranian Cyber Groups
Mandiant’s report highlights UNC1860’s connections to APT34, another Iranian cyber espionage group. Both groups have targeted entities in Iraq, Saudi Arabia, and Qatar, with UNC1860’s compromised systems serving as a bridge for further exploitation.
Potential Connection to High-Profile Cyber Attacks
While direct involvement in major cyber attacks like the October 2023 wiper attack on Israel or the ROADSWEEP attacks in Albania cannot be independently verified, UNC1860’s tools appear to be designed to enable such operations. The group’s ability to gain initial access makes them a valuable asset in Iran’s cyber arsenal.
Implications and Recommendations
The activities of UNC1860 underscore the evolving threats posed by state-sponsored cyber espionage. Organizations must prioritize cybersecurity resilience by:
- Enhancing detection capabilities to identify and mitigate passive utilities used by UNC1860 and other threat actors.
- Implementing robust endpoint security measures to prevent unauthorized access and lateral movement.
- Regularly updating software and firmware to patch vulnerabilities that could be exploited by threat actors.
Conclusion
As geopolitical tensions persist, organizations must remain vigilant against the increasing sophistication of Iranian cyber operations. UNC1860 serves as a reminder of the importance of proactive cybersecurity measures to safeguard organizational integrity and resilience from such sophisticated threats.