On December 6, 2023, the cybersecurity experts at Wordfence identified a concerning changelog entry for Elementor, a widely-used WordPress plugin installed on nearly 9 million websites. The entry, pertaining to version 3.18.1, hinted at a security vulnerability that had the potential to compromise the integrity of countless online platforms. Wordfence’s subsequent investigation revealed a partially effective patch, prompting swift action to protect their user base. CVE-2023-48777
The Vulnerability CVE-2023-48777
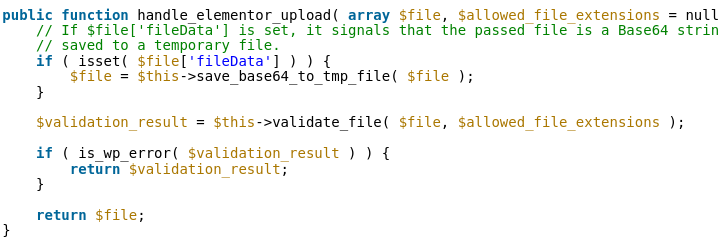
The identified vulnerability lay in Elementor’s template import functionality, allowing authenticated attackers with Contributor-level privileges or higher to exploit the system through remote code execution via file upload. The flaw originated from the handle_elementor_upload function, accessible to Contributor-level users and above. Despite initial attempts to patch the issue in version 3.18.1, the safeguard proved inadequate, requiring further attention.
Wordfence promptly responded to the partial patch by releasing a firewall rule to their Premium, Care, and Response customers. However, recognizing the insufficiency of the fix, they expedited communication with the Elementor team on the same day of discovery, emphasizing the need for a more comprehensive solution.
Elementor’s Swift Response
To their credit, Elementor reacted promptly to Wordfence’s alert, releasing version 3.18.2 on December 8, 2023. This update included a sufficient patch to rectify the vulnerability, showcasing the Elementor team’s commitment to addressing security concerns promptly.
Technical Analysis
The technical analysis revealed that the exploit allowed contributors to upload files of any type, saved in a temporary directory with a randomized name. The initial patch attempted to sanitize filenames, restricting uploads to the temporary directory. However, the flaw persisted, as the system failed to delete the temporary file if it failed validation, making it susceptible to exploitation.
The severity of this vulnerability cannot be overstated, as it could empower attackers to take control of a site. While the risk is mitigated by the requirement for Contributor-level privileges or higher, Wordfence urges all Elementor users to update to the latest version, 3.18.2, as a precautionary measure.
Wordfence’s Protection Measures
Wordfence has proactively shielded its users, including Premium, Care, and Response subscribers, against this vulnerability. Free Wordfence users will receive the firewall rule 30 days after the initial release to further safeguard their websites.
In conclusion, the collaboration between Wordfence and Elementor serves as a testament to the importance of vigilance in the ever-evolving landscape of cybersecurity. Users of the Elementor WordPress plugin are strongly advised to update to version 3.18.2 immediately to ensure the security and integrity of their websites. This incident underscores the critical role that timely communication and comprehensive solutions play in safeguarding the digital ecosystem against potential threats.