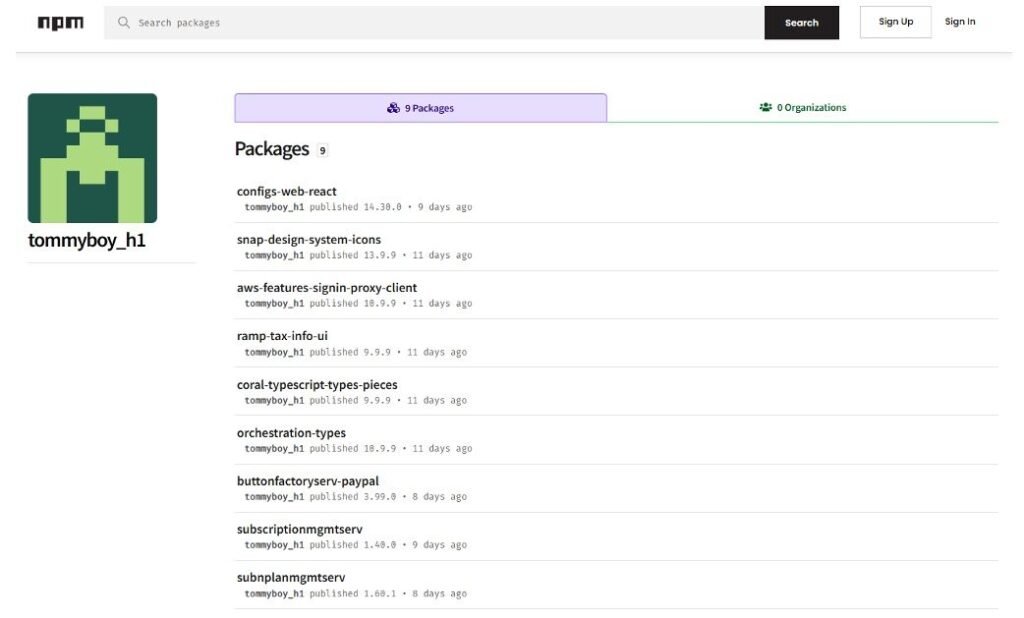
FortiGuard Labs recently uncovered a series of malicious NPM packages designed to steal sensitive information from compromised systems. These packages, created between March 5 and March 14, were attributed to a threat actor operating under the aliases “tommyboy_h1” and “tommyboy_h2.” The primary targets of these attacks are PayPal users, leveraging the platform’s widespread use and its repository of sensitive financial data.
The Attack Vector
The attackers exploited a clever social engineering tactic by naming their malicious packages with PayPal-related keywords, such as oauth2-paypal and buttonfactoryserv-paypal. This naming strategy creates a false sense of legitimacy, tricking developers into installing these packages. Once installed, the malicious code executes automatically via a “preinstall hook,” bypassing user detection and security measures.
How the Malware Operates
The malicious script embedded in these packages performs the following actions:
- Data Collection: It gathers system information, including usernames, hostnames, working directories, and other directory paths.
- Obfuscation: The collected data is encoded in hexadecimal format and further obfuscated by truncating and splitting directory paths to evade detection.
- Exfiltration: The obfuscated data is sent to an attacker-controlled server via dynamically generated URLs, making it difficult for security tools to block.
This stolen information can be used to compromise PayPal accounts or sold for fraudulent purposes.
Indicators of Compromise
To identify a potential compromise:
- Look for unusual NPM packages with names referencing PayPal (e.g., oauth2-paypal or buttonfactoryserv-paypal).
- Monitor network logs for unexpected connections to unknown servers.
- Investigate any suspicious activity involving newly installed dependencies.
Mitigation Steps
If you suspect a system has been compromised:
- Remove the malicious package immediately.
- Change any potentially exposed credentials.
- Scan your system for additional threats using updated security tools.
- Ensure your antivirus and web filtering services are current to prevent future attacks.
This campaign highlights the importance of vigilance when installing third-party packages. Developers should always verify the source of dependencies and monitor for unusual activity in their environments. By staying informed and maintaining robust cybersecurity practices, organizations can mitigate risks posed by such sophisticated attacks.