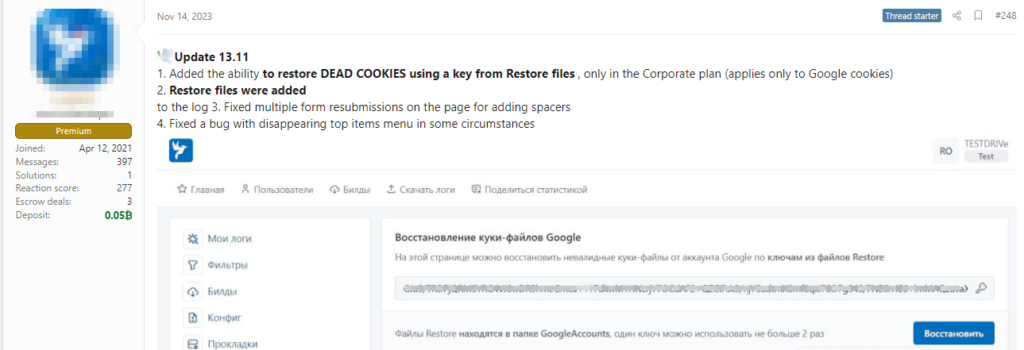
In a troubling development, cybersecurity researchers have uncovered a growing threat to Google account security, as multiple malware-as-a-service (MaaS) information stealers now possess the capability to manipulate authentication tokens. This newfound ability allows hackers to maintain persistent access to a victim’s Google account, even after the user has taken measures such as password resets.
Since November, one of the primary culprits identified is the Lumma Stealer, a notorious information-stealing malware offered as a service. The revelation comes from cybersecurity firm CloudSEK, whose researchers have raised concerns about the exploitation of the OAuth 2.0 security protocol. OAuth 2.0 is widely utilized for single sign-on, enabling seamless access to Google-connected accounts.
The Lumma Stealer is noteworthy for being the first malware-as-a-service to incorporate the manipulation of “undocumented OAuth2 functionality” through a technique known as “blackboxing.” This method conceals the malicious activities, adding a layer of sophistication to the exploit and making it harder to detect. CloudSEK emphasized that this strategic move not only establishes Lumma Stealer’s uniqueness in the cybercrime landscape but also provides an advantage in the illicit market.

CloudSEK’s research indicates that despite Lumma Stealer’s blackboxing approach, other malicious actors and malware distribution groups have swiftly adopted this vulnerability. Notable mentions include Rhadamanthys, RisePro, Meduza, Stealc Stealer, and Eternity Stealer, the latter explicitly announcing its plans to integrate this functionality.
The origin of the vulnerability traces back to a threat actor using the pseudonym PRISMA, who revealed a zero-day exploit for the flaw in a Telegram channel post in late October. PRISMA’s exploit enables what is referred to as “session persistence.” This means that even if a user changes their password, the attacker can maintain unauthorized access by generating valid authentication cookies, allowing them to circumvent disrupted sessions.
Pavan Karthick M, a threat researcher for CloudSEK, stressed the severity of the impact, stating that compromised Google accounts could be exploited to access sensitive information such as Drive, email, and other OAuth-connected services. Furthermore, infected accounts could be utilized as part of a malicious infrastructure, enabling threat actors to post malicious content, abuse streaming services, and gain unauthorized access to various Google-connected platforms.
The evolving nature of these exploits underscores the ongoing challenges in safeguarding digital identities. As users and organizations rely increasingly on interconnected services, it becomes imperative for cybersecurity professionals to stay vigilant and proactive in addressing emerging threats. At the time of reporting, Google has not responded to requests for comments on the matter.
As the cybersecurity landscape continues to evolve, users are advised to remain vigilant, implement multi-factor authentication, and promptly update their security measures to mitigate the risk of falling victim to these sophisticated and persistent attacks.