At the 37th Chaos Communication Congress, cybersecurity experts Boris Larin, Leonid Bezvershenko, and Georgy Kucherin from Kaspersky Lab have exposed a highly sophisticated and unprecedented espionage campaign targeting iPhones. Dubbed “Operation Triangulation,” this intricate attack chain utilized undisclosed Apple chip functions to circumvent hardware security measures, marking it as the most sophisticated attack chain ever witnessed.
The primary objective of Operation Triangulation, which commenced as early as 2019, was to discreetly implant a spy module into iPhones belonging to company employees, including top and mid-level management. The attack vector exploited a complex method of distributing exploits through iMessage messages, requiring no user interaction for activation.
Kaspersky Lab had previously released detailed reports on TriangleDB malware, elucidating how the implant was loaded onto devices after attackers gained root access through a vulnerability in the iOS kernel. Another report delved into the stealth and tools employed by hackers, dissecting the implant’s post-compromise activity.
Five critical vulnerabilities, including CVE-2023-32434, CVE-2023-32435, CVE-2023-38606, and CVE-2023-41990, were identified and promptly addressed by Apple. The severity of these vulnerabilities ranged from potential arbitrary code execution with kernel privileges to the manipulation of sensitive kernel state.
Of particular interest was CVE-2023-38606, a vulnerability addressed on July 24, 2023, with the release of iOS and iPadOS 16.6. This flaw revealed a striking evolution in the attackers’ techniques, as new iPhone models boasted additional hardware protection for sensitive kernel memory areas. This safeguard prevented full control of the device, even in cases where attackers gained read-write access to kernel memory.
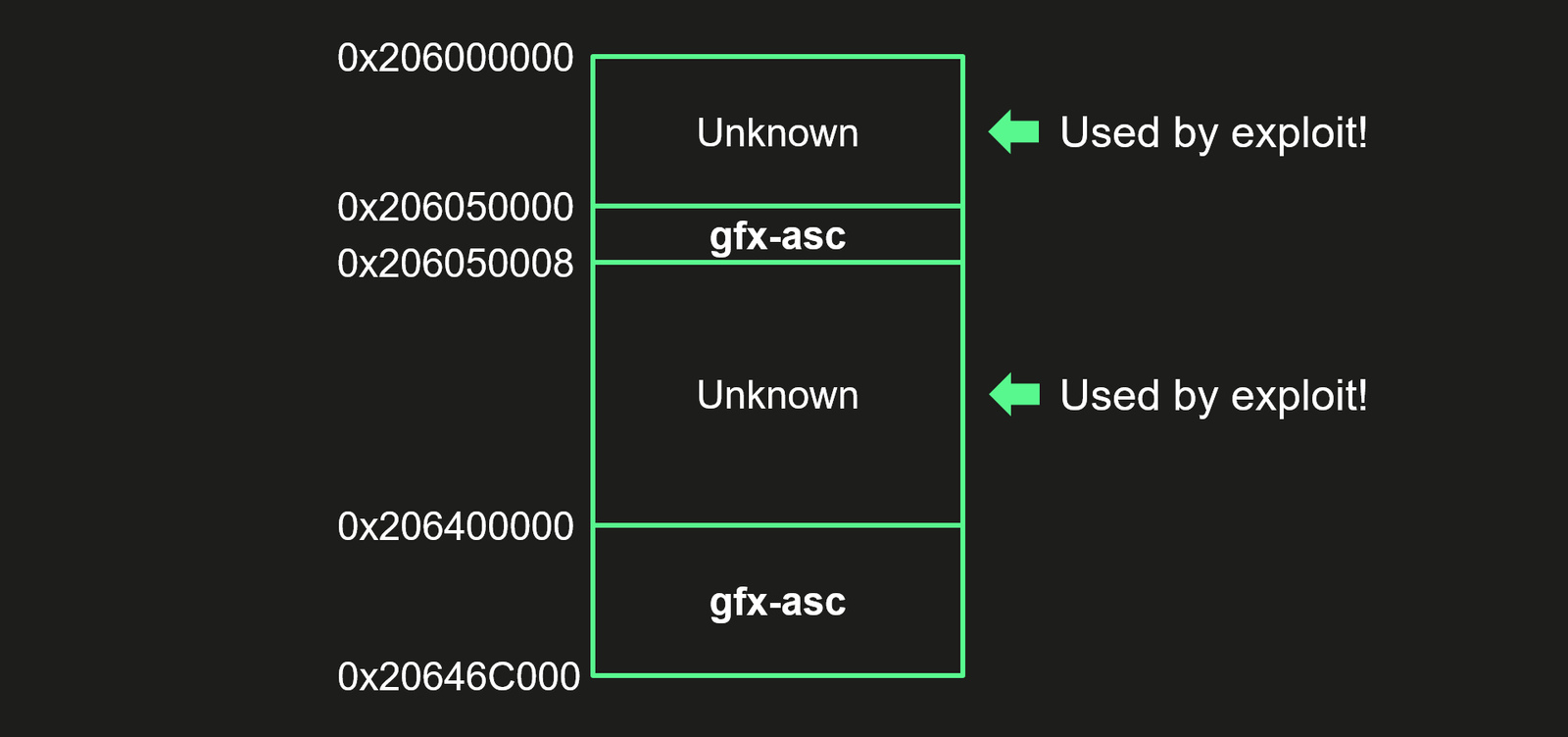
Researchers discovered that hackers bypassed this enhanced hardware protection by exploiting an undocumented Apple SoC hardware function. This function allowed attackers to write necessary data to a specific physical address, effectively sidestepping memory hardware protection. By utilizing firmware-unused hardware registers of the chip, the attackers wrote data, destination addresses, and data hashes.
The particularly puzzling aspect of this revelation was the undisclosed nature of the hardware function. Researchers speculated that it may have been intended for debugging or testing by Apple engineers or during manufacturing. However, its inactivity in the firmware left experts perplexed, acknowledging having “no idea” how attackers discerned its use without any instructions.
The technical part of the report elucidated that CVE-2023-38606 targeted unknown MMIO (memory-mapped input/output) registers in Apple A12-A16 Bionic, linked to the GPU coprocessor but absent in the device tree.
As analysts near completion of the reverse engineering process, they plan to release a series of articles detailing each vulnerability and its exploitation. Despite this progress, certain aspects of CVE-2023-38606 remain elusive, underscoring the relentless cat-and-mouse game between cyber attackers and defenders in the ever-evolving landscape of digital security.
In response to this unprecedented threat, Apple has demonstrated its commitment to user safety by swiftly addressing and patching the identified vulnerabilities. However, the revelation of Operation Triangulation serves as a stark reminder of the ever-present challenges in securing our increasingly interconnected digital lives. The cybersecurity community must remain vigilant and proactive to stay one step ahead of the adversaries who continually seek to exploit unforeseen weaknesses in our digital infrastructure.