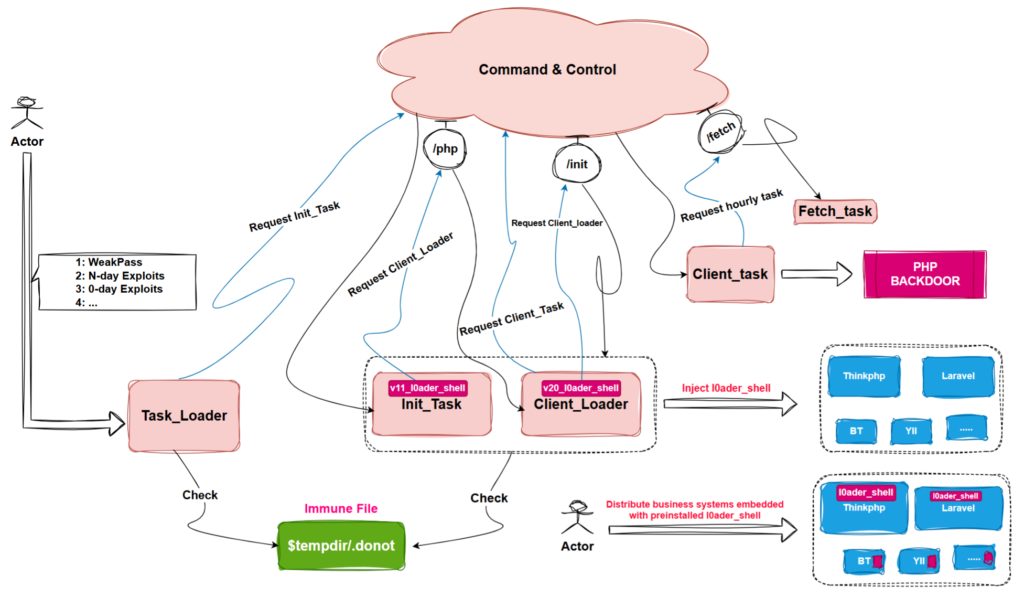
On April 29, 2024, XLab’s threat analysis system detected unusual activities linked to a new malware named Glutton, designed to stealthily infiltrate popular PHP frameworks. This malware was discovered while distributing a malicious PHP file, titled init_task.txt, which went undetected by security systems.
Attack details
Analysis revealed that Glutton is capable of infecting numerous PHP files and installing both ELF-based and PHP-based backdoors. Its main features include:
- Data exfiltration: collects system information, operating system versions, and credentials from management panels like Baota.
- Backdoor installation: incorporates both ELF and PHP backdoors, increasing the attack’s complexity.
- Code injection: targets popular PHP frameworks such as Baota, ThinkPHP, Yii, and Laravel.
The identified malware sample showed significant similarities to tools previously associated with the APT group Winnti, suggesting a possible attribution to this group. However, Glutton exhibits some weaknesses in terms of stealth and implementation, such as the lack of encrypted C2 communications and un-obfuscated PHP samples, making its analysis more accessible to security experts.
Targets and implications
Infections from Glutton have primarily been identified in the United States and China, affecting sectors such as IT services and social security. A concerning aspect that emerged from the investigation is that the creators of Glutton deliberately targeted systems within the cybercrime market, aiming to “poison” the operations of other cybercriminals. This approach has led to a situation where cybercriminals themselves become victims of their own weapons.
Glutton represents a new threat in the cybersecurity landscape, highlighting the increasing complexity of modern cyberattacks. Its ability to exploit existing vulnerabilities in PHP frameworks and its strategy of targeting even other cybercriminals raise questions about the overall security of the sector. Experts warn that continuous vigilance is essential to prevent further compromises and to protect critical infrastructures from such sophisticated threats.