Read Time:1 Minute, 27 Second
A newly discovered vulnerability class, termed “False File Immutability” (FFI), has been identified by Gabriel Landau of Elastic Security, exposing a significant flaw in Windows Code Integrity (CI). This vulnerability allows attackers to circumvent CI, a critical security mechanism in Windows, by exploiting erroneous assumptions about file immutability.
Key Points
- False Assumption of Immutability: The FFI vulnerability arises from the incorrect belief that files opened without FILE_SHARE_WRITE permissions cannot be modified. However, attackers can exploit race conditions and file attribute manipulations to alter these files.
- Double-Read Vulnerabilities: FFI exploits double-read vulnerabilities, where the same file value or offset is read multiple times, leading to potential inconsistencies and exploitation opportunities.
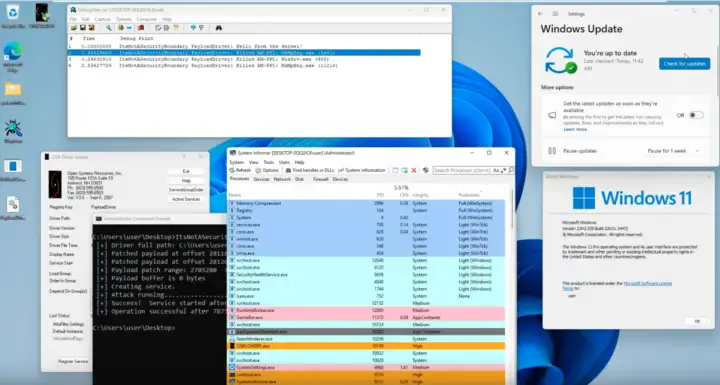
- Impact on Code Integrity: The proof-of-concept exploit, “ItsNotASecurityBoundary,” demonstrates how FFI can manipulate Windows Code Integrity (ci.dll). By injecting malicious code into a trusted security catalog, attackers can bypass signature verification and load arbitrary, unsigned drivers.
- Exploitation Method: The exploit requires precise timing and a complex sequence of events. It manipulates CI into accepting a fraudulent security catalog with fake authentihashes, tricking the kernel into loading malicious drivers.
- Potential Consequences: Successful exploitation allows attackers to disable security software, evade detection, and deploy malware, compromising the entire system’s integrity and security.
- Mitigation: As a temporary solution, Landau has released a kernel driver, “FineButWeCanStillEasilyStopIt,” which detects and blocks the exploit by monitoring suspicious file modifications. However, a comprehensive fix within Windows Code Integrity is necessary for a permanent resolution.
Conclusion
The discovery of FFI highlights a critical vulnerability in Windows Code Integrity. Immediate measures, such as using Landau’s kernel driver, can mitigate the risk temporarily. However, a fundamental fix within the Windows CI mechanism is essential to fully address this vulnerability and safeguard system integrity.