A severe zero-click vulnerability has been discovered within Apple’s macOS Calendar application, posing a significant threat to user security. This vulnerability enables attackers to compromise user devices without requiring any interaction, potentially leading to the execution of malicious code and data theft.
Vulnerability Details
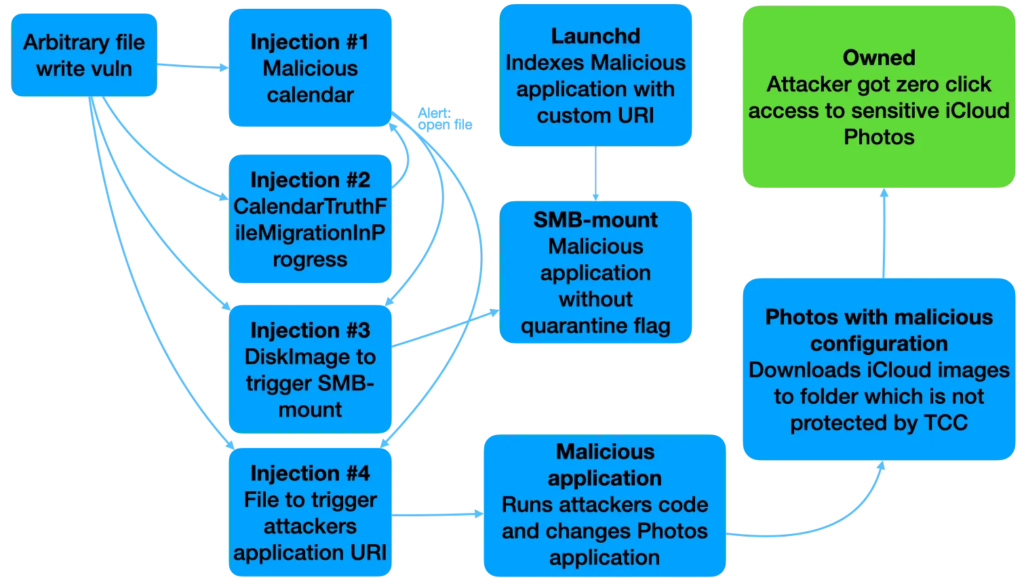
The vulnerability, identified as CVE-2022-46723, allows attackers to leverage unsanitized file attachments in calendar invites to perform directory traversal attacks. This allows them to overwrite or delete files within the Calendar app’s filesystem.
Exploitation Sequence
The exploit involves sending a malicious calendar invite containing an attachment with an intentionally crafted filename. This enables the attacker to bypass security protections and place malicious files within the victim’s filesystem.
Attackers can exploit this vulnerability to:
- Escalate privileges and inject malicious calendar files that execute code during macOS upgrades.
- Trigger remote code execution (RCE) by launching malicious .dmg images or .url shortcuts within injected calendar events.
Impact on iCloud Photos
Security researcher Mikko Kenttala demonstrated how the vulnerability could be combined with a flaw in Apple’s Photos app to leak private iCloud photos. By changing Photos settings to an unprotected directory, attackers could bypass TCC protection and access user data.
Apple’s Response
Apple has released patches between October 2022 and September 2023 to address all vulnerabilities related to CVE-2022-46723. These patches tighten file permissions and implement additional security measures to prevent directory traversal exploits.
Mitigation Measures
To protect against zero-click vulnerabilities like this one, it is essential to: - Keep software up to date and install security patches promptly.
- Restrict app access to sensitive data, such as calendars and photos.
- Employ a multi-layered security approach to mitigate emerging threats.
Conclusion
The macOS Calendar zero-click vulnerability highlights the growing sophistication of cyberattacks targeting user data. By staying vigilant, promptly applying security updates, and adopting proactive security measures, individuals and organizations can safeguard their devices and data from these evolving threats.