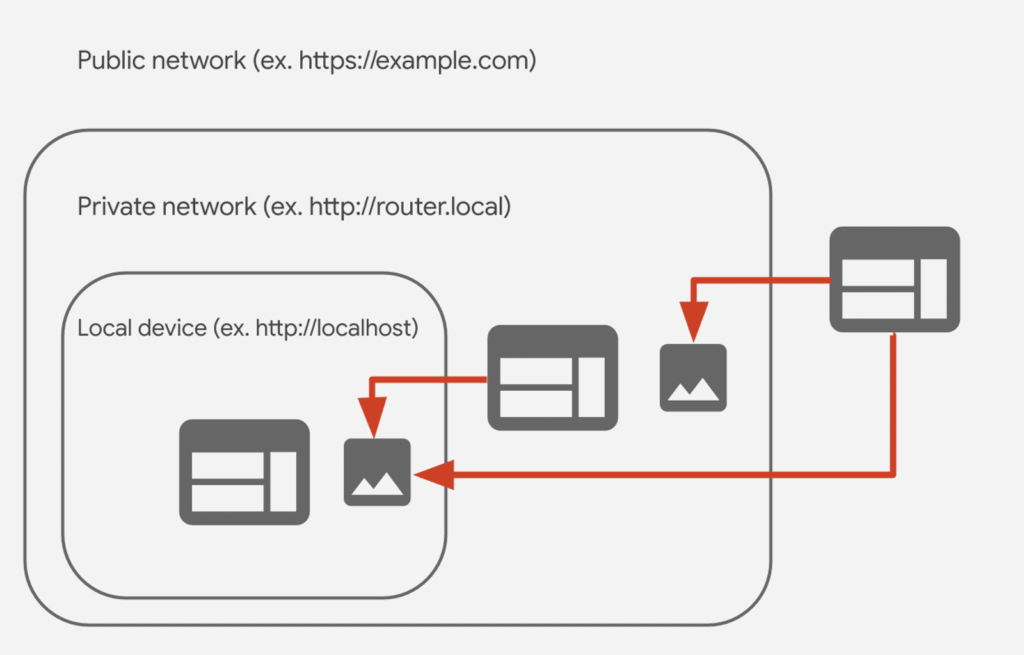
A recent study by Oligo Security has revealed a critical vulnerability impacting the world’s leading web browsers for the past 18 years. Dubbed the “0.0.0.0 Day” vulnerability, this issue arises from the way browsers manage requests directed to the IP address 0.0.0.0, which can be exploited by hackers to redirect traffic covertly to local servers, such as “localhost.” This manipulation poses significant risks, enabling attackers to lure users to malicious sites that send hidden requests through this address, potentially exposing sensitive information, such as developer data and internal communications.
The implications of this vulnerability are staggering, as it grants unauthorized access to users’ internal networks, creating numerous attack vectors. Both individuals and organizations operating web servers are affected, with the potential for malicious code execution demonstrated using the Ray AI framework. This is a widespread concern, as any application reachable via 0.0.0.0 is susceptible.
While Google’s security team has already flagged cases of malware exploiting this weakness, Windows users remain protected, as Microsoft blocks 0.0.0.0 by default. In response to the threat, Apple plans to implement restrictions in the upcoming macOS 15 Sequoia beta, and Google is contemplating similar protections for its Chromium and Chrome browsers. Contrastingly, Mozilla is wavering on the issue due to compatibility concerns with servers that utilize this address.
The urgency of addressing this vulnerability is underscored by researchers who emphasize the considerable risk still posed to unprotected systems, as extensive pools of previously secured data remain vulnerable. The situation will be discussed in further detail at the DEF CON conference in Las Vegas, where cybersecurity experts will brainstorm mitigation strategies regarding this long-standing issue. As developments unfold, stakeholders must remain vigilant and informed about this critical security concern.