Read Time:1 Minute, 34 Second
In a joint cybersecurity advisory, the FBI, Cyber National Mission Force (CNMF), and National Security Agency (NSA) have exposed a significant threat to Internet-connected devices. Chinese hackers have compromised thousands of devices, creating a colossal botnet used for malicious activities.
Compromised Devices and Botnet Capabilities
The botnet comprises an array of compromised devices, including:
- Small office/home office (SOHO) routers
- Firewalls
- Network-attached storage (NAS)
- Internet of Things (IoT) devices
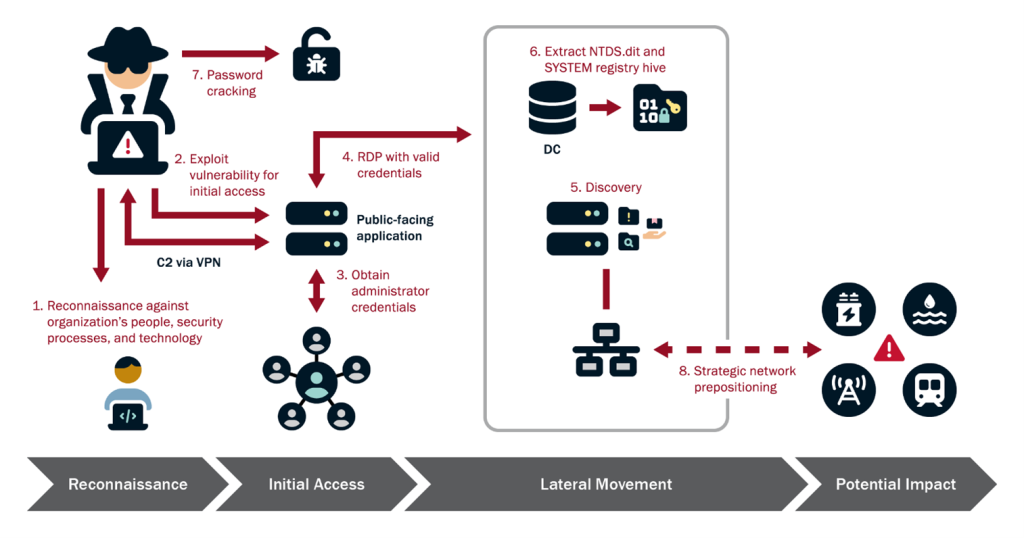
The botnet, managed by Integrity Technology Group (a PRC-based company), has remained active since mid-2021 and maintains hundreds of thousands of compromised devices. As of June 2024, the botnet had over 260,000 devices worldwide.
Vulnerability Exploits and Malware
The hackers exploited various known software vulnerabilities, such as those in Zyxel, Fortinet, and QNAP devices, to compromise these devices. Compromised devices were infected with a customized version of the Mirai malware, which grants threat actors remote control over the devices.
Command and Control Infrastructure
The botnet’s command and control (C2) servers were managed using a tier of upstream management servers hosting a MySQL database with information on compromised devices. Chinese IP addresses were used to access the “Sparrow” botnet management application.
Mitigations and Recommendations
The advisory provides detailed recommendations for protecting against this botnet, including: - Disabling unused services and ports
- Implementing network segmentation
- Monitoring for high network traffic volume
- Applying patches and updates
- Replacing default passwords with strong credentials
Importance of Cybersecurity Measures
This incident highlights the growing threat of state-sponsored cyberattacks. Organizations and individuals must implement robust cybersecurity measures, including: - Regularly updating and patching systems
- Implementing multi-factor authentication
- Using strong passwords
- Conducting regular vulnerability assessments
- Educating employees on cybersecurity best practices
Call to Action
Device owners and operators are strongly urged to take immediate action to secure their devices and prevent further compromise. By implementing cybersecurity measures and following the recommendations outlined in the advisory, we can collectively reduce the risk of these devastating attacks.