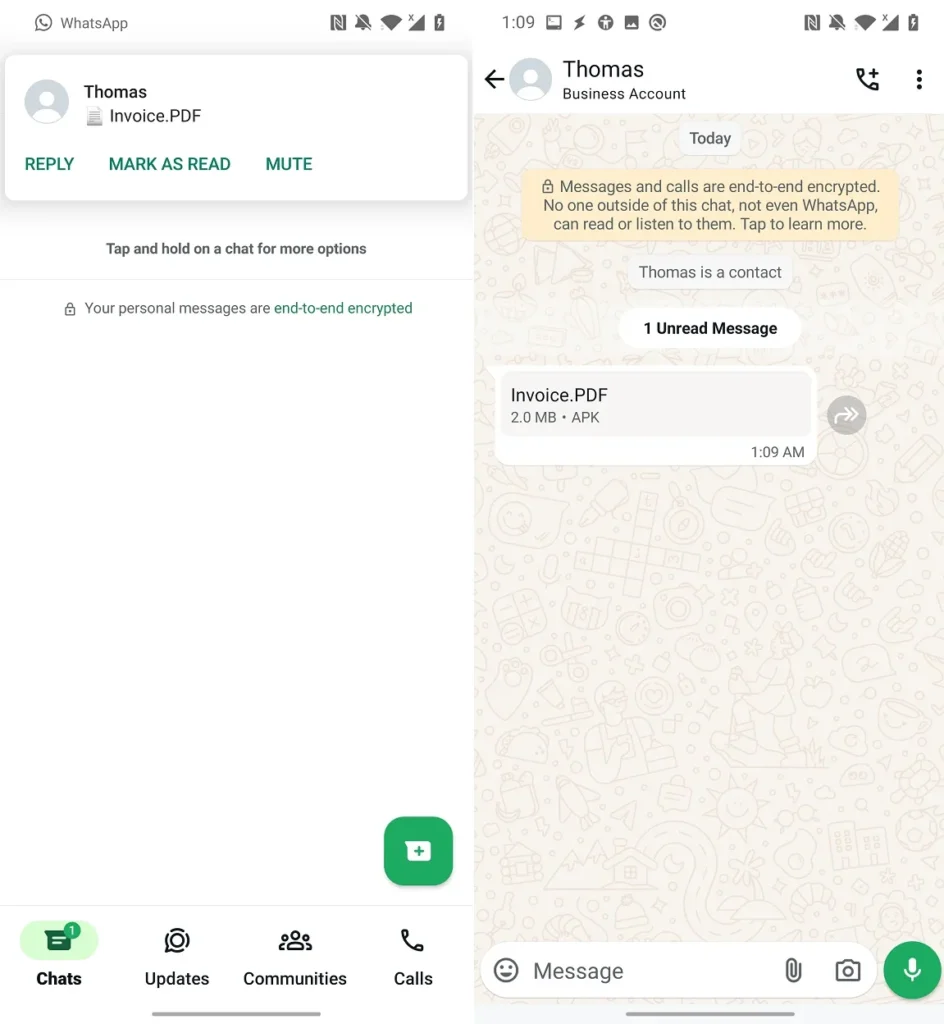
In a recent discovery that has raised concerns within the cybersecurity community, malware analyst @0x6rss identified a significant security issue in WhatsApp Messenger for Android. This vulnerability allows an attacker to disguise a malicious Android app as a PDF file shared within a chat. While this method does not enable direct attachment of malicious apps through normal use of WhatsApp, it poses a substantial risk through a more sophisticated approach.
Details of the Vulnerability
The issue was discovered and shared by @0x6rss on X (formerly Twitter) on July 14, 2024. The core of the vulnerability lies in the ability to manipulate WhatsApp’s programming interface to send a specially crafted request. This request can disguise a harmful Android app as a seemingly innocuous PDF file in a chat.
On June 25, 2024, @0x6rss reported this “extension manipulation bug” to Facebook’s security team, which oversees WhatsApp’s bug bounty program. Despite the apparent severity, the team categorized the issue as a type of social engineering, rather than a security vulnerability within the scope of their bug bounty program. This classification implies that while the method is deceptive, it is not considered a direct threat by the standards of their current security criteria.
Implications for Users
Despite the official stance, the potential for harm is significant, especially for users who may not be well-versed in technology. The simplicity and effectiveness of this trick can lead to unsuspecting users downloading and installing malicious applications, believing them to be harmless PDF files. This can result in various consequences, from data theft to the complete compromise of the user’s device.
A similar issue was recently discovered and addressed by Telegram, where malicious Android apps could be disguised as video files in chats. The quick response from Telegram highlights the importance of recognizing and mitigating such vulnerabilities promptly.