In the ever-evolving realm of cyber threats, a malevolent force known as PlugX has emerged, weaving a complex tapestry of espionage and evasion that has left cybersecurity experts perplexed. Recently, the Splunk Threat Research Team (STRT) embarked on a journey to unravel the mysteries surrounding a new variant of PlugX, shedding light on its sophisticated features and its ability to skillfully navigate the digital landscape undetected.
At the heart of PlugX’s nefarious capabilities lies its mastery of process masquerading, a technique that enables it to seamlessly integrate itself into legitimate Windows services such as ‘msdtc.exe.’ This insidious maneuver not only facilitates covert operations but also ensures the malware’s persistence, evading conventional detection methods with a cloak of legitimacy.
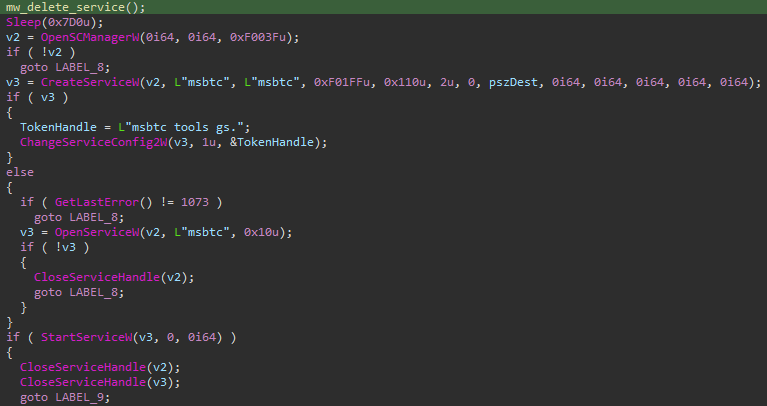
The decryption of the headless PlugX payload from ‘msbtc.dat’ reveals a strategic move by the malware as it injects itself into ‘msdtc.exe,’ the Microsoft Distributed Transaction Coordinator. This crucial Windows service manages distributed transactions across diverse resources, from databases and message queues to file systems, providing PlugX with an ideal cover for its clandestine activities.
PlugX’s prowess extends beyond mere infiltration, as it demonstrates a knack for gathering sensitive information, including network details and user credentials. The malware takes impersonation to new heights, assuming the identity of the logged-in user, escalating privileges, and accessing critical system resources with a chilling efficiency.
A standout feature in PlugX’s arsenal is its keylogging capability, silently recording keystrokes and monitoring processes to amass valuable data without triggering any user alerts. This clandestine data collection adds a layer of sophistication to its cyber espionage toolkit, enabling it to operate undetected and gather intelligence with precision.
To maintain a surreptitious line of communication with its command and control server, PlugX employs a shrewd manipulation of firewall rules. The malware strategically adds a rule labeled “Microsoft Edge,” configured to permit incoming network traffic for a specific TCP port crucial for communication with the Command and Control (C2) server. This calculated manipulation of firewall settings ensures uninterrupted operations, allowing PlugX to exfiltrate data, execute commands, and potentially engage in additional malicious activities.
The blog post analysis concludes by emphasizing that PlugX serves as a stark reminder of the advanced nature of modern cyber threats. Its ability to don a disguise, gather sensitive data, and persistently operate within compromised systems underscores the ever-evolving challenges faced by cybersecurity professionals. In this intricate dance between defenders and attackers, staying vigilant and understanding the tactics of such insidious malware is paramount to securing the digital frontier.