FrigidStealer represents a sophisticated evolution in macOS-targeted malware, combining social engineering with technical evasion tactics to compromise sensitive data. First observed in January 2025, this information stealer masquerades as browser updates through compromised websites, delivering malicious DMG files that bypass macOS Gatekeeper protections via AppleScript password prompts. The malware demonstrates several concerning characteristics:
Operational Behavior
- Persistence Mechanism: Registers as
ddaolimaki-daunitowith bundle IDcom.wails.ddaolimaki-daunito, leveraginglaunchservicesdfor foreground execution1. - Data Targeting: Uses Apple Events for unauthorized IPC to harvest:
- Browser credentials (Chrome, Safari, Firefox) – Cryptocurrency wallet files – System information (macOS version, hardware specs) – Keychain access attempts
- Exfiltration Technique: Utilizes
mDNSResponderfor DNS-based data exfiltration to C2 infrastructure, followed by process termination (ddaolimaki-daunito) to erase execution artifacts.
Technical Indicators
| Indicator Type | Value |
|---|---|
| SHA256 Hash | e1202c017c76e06bfa201ad6eb824409c2529e887bdaf128fc364bdbc9e1e2141 |
| Persistence Path | /Volumes/Safari Updater/Safari Updater.app |
| C2 Communication | DNS queries via mDNSResponder with masked hash values1 |
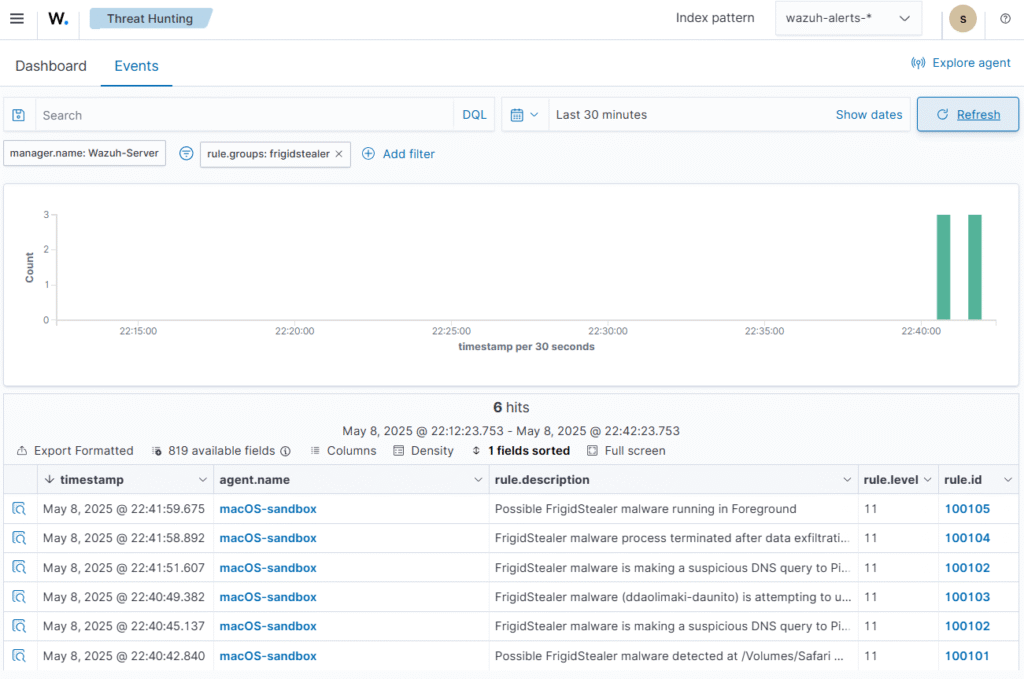
Detection Strategy with Wazuh
The implemented detection rules focus on key behavioral patterns:
<!-- Rule 100102: DNS exfiltration -->
<rule id="100102" level="11" frequency="2" ignore="60">
<decoded_as>macOS_mDNSResponder</decoded_as>
<field name="process_name">ddaolimaki.*</field>
<description>DNS data exfiltration to $(hash)</description>
</rule>
<!-- Rule 100105: Persistence detection -->
<rule id="100105" level="11">
<match>"LSBundlePath"="(.*Safari Updater.app)"</match>
<field name="bundle_id">com.wails.ddaolimaki-daunito</field>
</ruleThese rules map to MITRE ATT&CK techniques T1071.004 (DNS C2) and T1543 (Persistence).
Evasion Tactics
- Uses legitimate macOS processes (
launchservicesd,mDNSResponder) for malicious operations - Self-terminates within 60 seconds of data exfiltration
- Stores payloads in
/private/var/folderswith randomized subdirectories
This multi-vector approach enables FrigidStealer to maintain operational effectiveness while evading basic signature-based detection. The Wazuh implementation demonstrates how layered monitoring of macOS unified logs (particularly launchd events and DNS query patterns) can surface these stealthy activities.