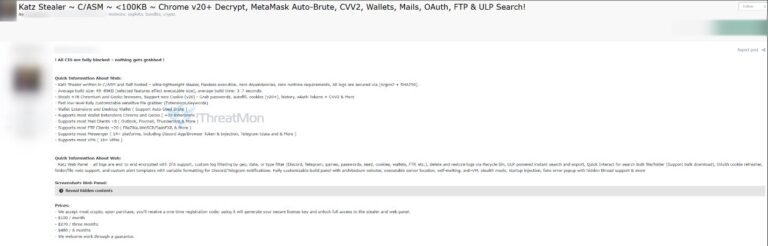
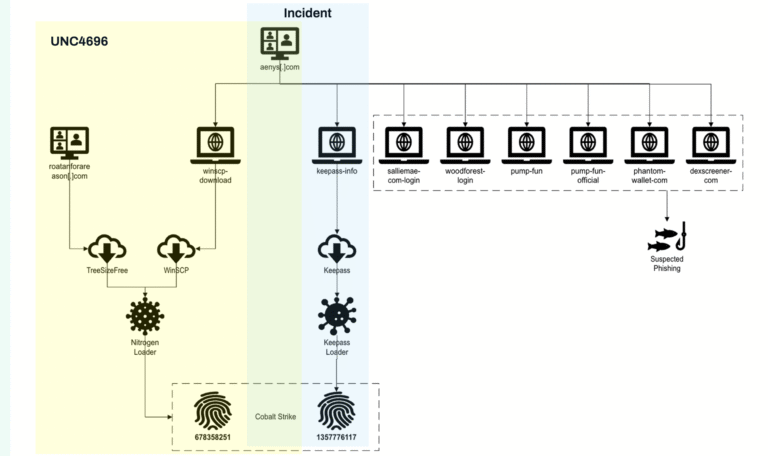
Latest news

Cybercrime
China-Linked APTs exploit critical SAP NetWeaver vulnerability to breach over 580 systems globally
13 May 2025 securebulletin.com
In a significant escalation of cyber-espionage activities, multiple China-affiliated advanced persistent threat (APT) groups have been found actively exploiting a...