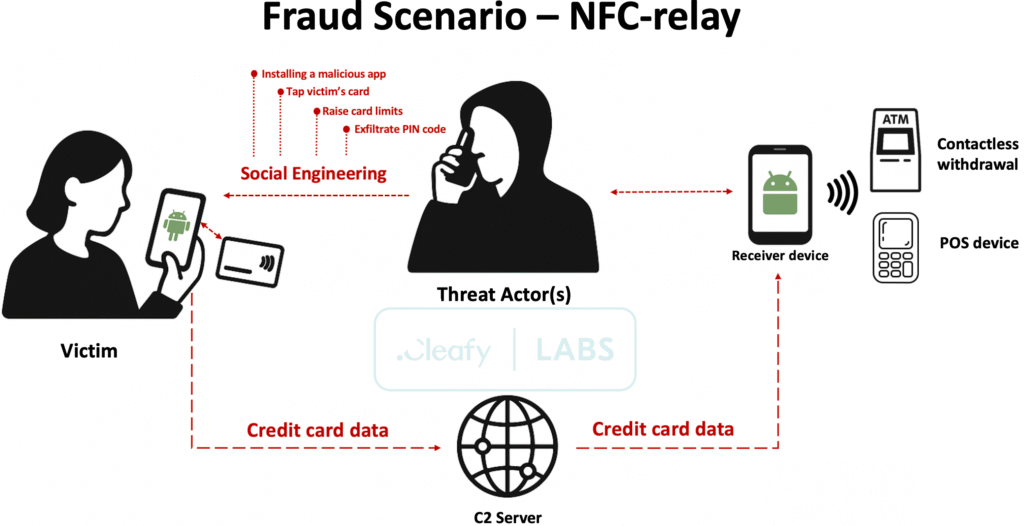
The Cleafy Threat Intelligence team has uncovered SuperCard X, a sophisticated Android malware campaign leveraging NFC-relay attacks to authorize fraudulent POS and ATM transactions. This Malware-as-a-Service (MaaS) operation1 primarily targets Italian banking customers but exhibits potential for global expansion due to its modular infrastructure.
Attack chain & technical mechanics
Social Engineering Onramp:
- Initiates via SMS/WhatsApp messages impersonating bank fraud alerts (TOAD attack vector)1
- Threat actors (TAs) guide victims to install the malicious “Reader” app (blue icon) under pretext of canceling fake transactions1
NFC Relay Infrastructure:
xml<!-- AndroidManifest.xml critical permission -->
<uses-permission android:name="android.permission.NFC" />
Dual-application architecture:
- Reader: Harvests NFC card data via compromised devices
- Tapper: TA-controlled app emulating stolen cards using relayed ATR messages1
C2 Communication:
- HTTP protocol with mutual TLS (mTLS) authentication
- Server rejects connections lacking client certificates (400 Bad Request)1
- Real-time data relay enables instant fraudulent transactions
Technical differentiators
- Low-Footprint Design: Only 7 Android permissions requested vs 20+ in typical banking trojans1
- ATR Spoofing: Embedded Answer-to-Reset messages bypass card-reader handshake checks1
- MaaS Customization: text
+ Italian variant removes "Register" button and Telegram references - Retains core NFC data exfiltration logic
Detection Evasion:
- 0/62 AV detection on VirusTotal at discovery
- Minimal behavioral patterns compared to SMS-hijacking malware
IoCs & campaign links
Malware Samples:
- SHA256: 7a8f3b… (Reader variant)
- SHA256: e29c41… (Tapper variant)
C2 Infrastructure:
- 185.65.135[.]88 (Port 443)
- hxxps://api-supercardx[.]com/auth/login
Code Heritage:
- 78% code overlap with NGate malware (ESET 2024)
- NFCGate open-source project code reuse
Defense implications
Financial institutions should:
- Implement NFC transaction velocity checks
- Monitor for abnormal ATR message patterns
- Update fraud detection systems to recognize instant cash-out patterns
- Conduct employee training on TOAD attack recognition
This campaign exemplifies the shift towards protocol-level exploitation over traditional credential theft. The combination of minimal permissions and legitimate NFC API abuse creates new detection challenges requiring behavioral analysis beyond signature-based methods.