In recent weeks, cybersecurity experts have identified a previously undocumented threat actor known as Silent Lynx, which has been linked to a series of sophisticated cyber attacks targeting entities in Kyrgyzstan and Turkmenistan. This emerging group appears to have its origins in Kazakhstan and is believed to be focused on espionage activities aimed at government institutions, financial organizations, and think tanks involved in economic decision-making.
Target profile and attack vectors
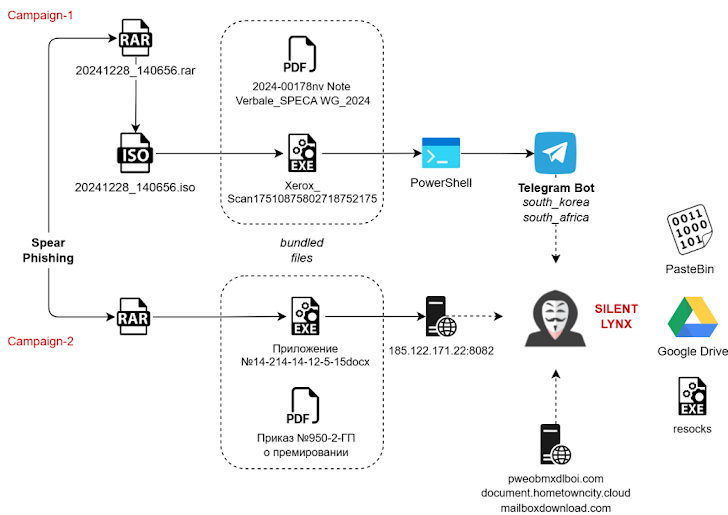
Silent Lynx has primarily targeted a variety of high-profile entities, including embassies, law firms, and government-backed banks. The group’s operations have raised concerns due to their strategic focus on institutions that play a crucial role in the region’s economic landscape. According to Seqrite Labs researcher Subhajeet Singha, the group’s tactics mirror those of other threat actors operating in Eastern Europe and Central Asia, particularly in their use of spear-phishing techniques to initiate attacks. The initial phase of their campaign typically begins with a spear-phishing email containing a RAR archive attachment. This archive serves as the delivery mechanism for malicious payloads designed to establish remote access to compromised systems. The first detected campaign, which began on December 27, 2024, utilized an ISO file embedded within the RAR archive. This ISO file contained a malicious C++ binary alongside a decoy PDF document. Once executed, the binary triggers a PowerShell script that leverages Telegram bots for command execution and data exfiltration.
Technical sophistication
Silent Lynx’s operations are characterized by a multi-stage attack strategy that highlights their technical sophistication. The use of PowerShell scripts and Golang executables is particularly noteworthy. In one variant of their attack, a decoy PDF is paired with a Golang executable designed to create a reverse shell connection to an attacker-controlled server. The reliance on Telegram bots for command and control communication is another significant aspect of their methodology. This choice not only facilitates covert operations but also allows for flexible command execution and data retrieval from compromised systems. Commands executed via these bots include downloading additional payloads from remote servers—an approach that underscores the group’s adaptive tactics.
Tactical overlaps with other threat actors
Interestingly, Seqrite Labs has observed tactical overlaps between Silent Lynx and another threat actor known as YoroTrooper (also referred to as SturgeonPhisher). Both groups have been linked to cyber operations targeting the Commonwealth of Independent States (CIS) countries, employing similar tools such as PowerShell and Golang.