Recent reporting from Google’s Threat Intelligence Group (GTIG) highlights a surge in activity from Russian state-aligned threat actors targeting Signal Messenger accounts. This campaign, likely driven by wartime intelligence demands related to the conflict in Ukraine, reveals sophisticated techniques aimed at intercepting sensitive communications. This analysis delves into the technical aspects of these attacks, their potential impact, and recommended mitigations.
Abusing Signal’s “Linked Devices” feature
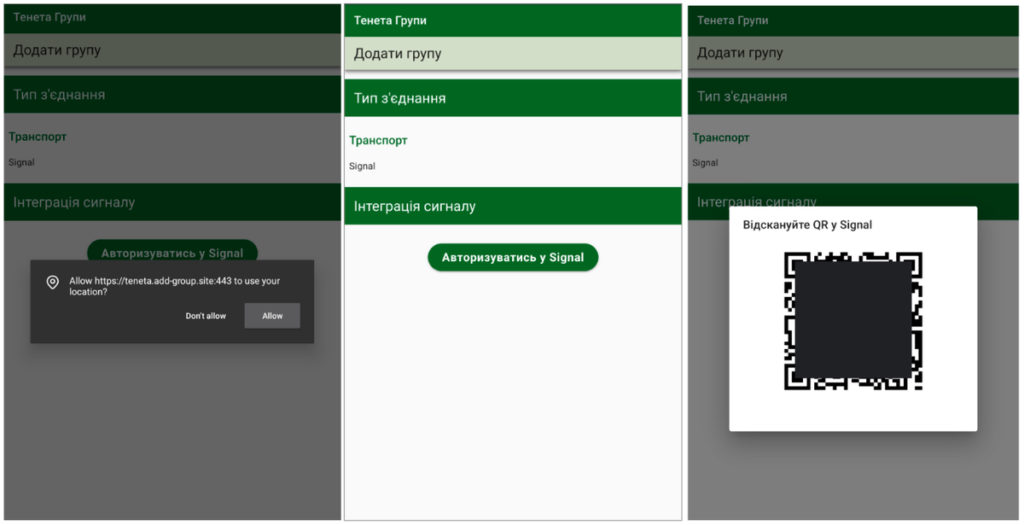
The core tactic observed involves exploiting Signal’s legitimate “linked devices” feature. Attackers use malicious QR codes to trick users into linking their accounts to attacker-controlled Signal instances. This grants the adversary real-time access to the victim’s messages without requiring full device compromise.
Technical breakdown:
- Phishing Vectors: malicious QR codes are often disguised as legitimate Signal resources:
- Fake group invites
- Security alerts
- Device pairing instructions mimicking the official Signal website.
- Tailored Phishing: in more targeted attacks, QR codes are embedded in phishing pages that impersonate applications used by the Ukrainian military (e.g., Kropyva).
- Close-Access operations: APT44 (Sandworm/Seashell Blizzard) has been observed using malicious QR codes on captured devices on the battlefield, linking them to Russian-controlled infrastructure.
- UNC5792: this group modifies legitimate “group invite” pages, replacing the standard redirection with a malicious URL (
sgnl://linkdevice?uuid=...) that links the victim’s device to the attacker’s. - UNC4221: this actor employs a custom-developed Signal phishing kit, mimicking components of the Kropyva application. This includes:
- Phishing sites redirecting to fake device-linking instructions.
- Embedded malicious QR codes within Kropyva-themed phishing pages.
- Earlier campaigns utilizing fake Signal security alerts.
- PINPOINT Payload: UNC4221 uses a lightweight JavaScript payload (PINPOINT) to gather user information and geolocation data via the browser’s GeoLocation API.
Data exfiltration techniques
Beyond the “linked devices” approach, threat actors also employ techniques to directly steal Signal database files from compromised devices.
- APT44 (Sandworm): Utilizes WAVESIGN, a Windows Batch script, to extract recent Signal messages from the database and exfiltrate them using Rclone.
- Infamous Chisel (Sandworm): This Android malware recursively searches for specific file extensions, including Signal’s local database, for exfiltration.
- Turla (FSB): Uses a PowerShell script in post-compromise scenarios to stage Signal Desktop messages for exfiltration.
- UNC1151 (Belarus-linked): Employs Robocopy to copy Signal Desktop file directories containing messages and attachments for later exfiltration.
Implications and mitigation
The increasing focus on Signal and other secure messaging apps highlights a growing trend in offensive cyber capabilities aimed at monitoring sensitive communications. This poses a significant threat to individuals relying on these platforms for secure communication.
Recommended mitigations:
- Strong device security: implement strong screen lock passwords (alphanumeric) on all mobile devices.
- Software Updates: keep operating systems and Signal (along with other messaging apps) updated to the latest versions.
- Google Play Protect: ensure Google Play Protect is enabled on Android devices.
- Regular audits: regularly audit linked devices in Signal’s settings for unauthorized entries.
- QR Code caution: exercise extreme caution when interacting with QR codes, especially those received via unsolicited communications.
- Two-Factor Authentication: enable two-factor authentication (fingerprint, facial recognition, security key, or one-time code) for account logins and device linking.
- Lockdown mode (iOS): iPhone users concerned about targeted surveillance should consider enabling Lockdown Mode.
The GTIG report underscores the evolving threat landscape surrounding secure messaging applications. The techniques employed by Russia-aligned actors demonstrate a clear intent to compromise Signal and similar platforms. Organizations and individuals should implement the recommended mitigations to protect their sensitive communications from these increasingly sophisticated attacks.