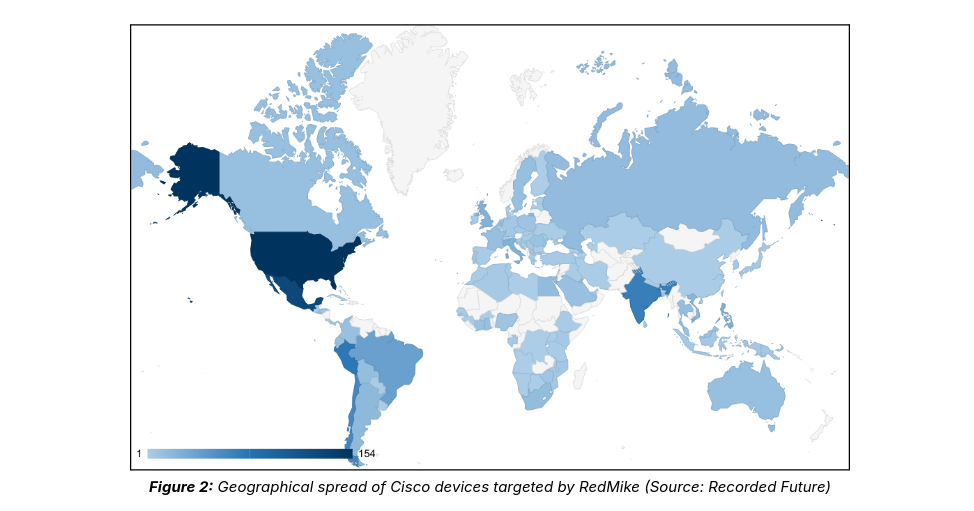
Despite widespread awareness and U.S. sanctions, the Chinese state-sponsored threat group RedMike (also known as Salt Typhoon) remains a persistent danger to telecommunications providers worldwide. Recent activity reveals RedMike actively exploiting vulnerabilities in unpatched Cisco network devices, including those within a U.S.-based affiliate of a UK telecommunications provider, and a South African provider. From December 2024 to January 2025, RedMike attempted to compromise over 1,000 Cisco devices globally.
Technical details
Insikt Group observed RedMike leveraging CVE-2023-20198 and CVE-2023-20273, privilege escalation vulnerabilities in Cisco IOS XE software, to gain initial access and root privileges. Successful exploitation allows RedMike to reconfigure devices, establishing persistent access via generic routing encapsulation (GRE) tunnels.
Italian implications
The report identifies an Italian ISP among the compromised telecommunications providers. This suggests Italian telecommunications infrastructure is actively targeted. RedMike’s ability to establish GRE tunnels raises concerns about potential covert communication channels bypassing traditional security measures like firewalls and intrusion detection systems. This could facilitate stealthy data exfiltration and persistent access for espionage or disruption.
Beyond telecommunications, RedMike targeted universities in multiple countries, including the Netherlands. This suggests a broader intelligence-gathering objective, potentially seeking research data related to telecommunications, engineering, and technology.
Strategic implications
RedMike’s continued activity underscores the strategic nature of these attacks. Persistent access to critical communications networks enables state-backed actors to:
- Monitor sensitive conversations
- Manipulate data flows
- Disrupt services during geopolitical conflicts
The group’s past targeting of U.S. lawful intercept programs and political figures highlights the high-value intelligence RedMike seeks.
Recommendations
To mitigate the threat posed by RedMike, organizations, particularly those in the telecommunications sector, should:
- Prioritize patching exposed network devices, especially Cisco devices running IOS XE software.
- Implement strict access controls and disable unnecessary web UI exposure.
- Monitor network traffic for unauthorized configuration changes and unfamiliar protocols like GRE.
- Use threat intelligence platforms to monitor for actively exploited technologies.
For Cisco IOS XE Devices
Network administrators should check system logs for suspicious login activity.
RedMike’s persistent targeting of telecommunications providers is expected to continue due to the wealth of valuable communications data these networks carry. The U.S. government’s response, including sanctions on RedMike-affiliated entities, signals a more assertive stance against state-backed cyber espionage. However, international cooperation and stricter regulatory compliance are crucial for effectively countering these persistent threats.