Latest news

Vulnerability
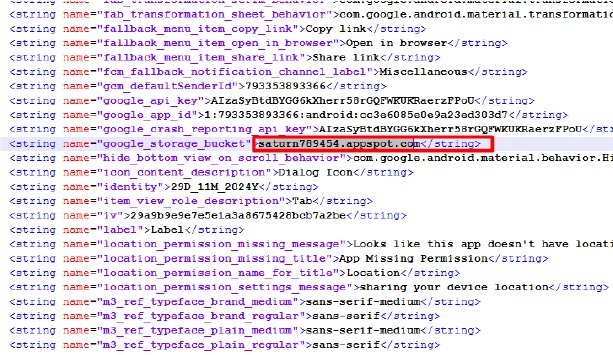
Kaspersky has revealed multiple vulnerabilities in the Mercedes-Benz User Experience (MBUX) infotainment system
20 January 2025 securebulletin.com
Recent reports have revealed significant vulnerabilities in the infotainment systems of Mercedes-Benz vehicles, raising concerns about potential cybersecurity threats. These...