In the ever-evolving landscape of cybersecurity threats, a recent report by ESET sheds light on the sophisticated tactics employed by the Iranian government-sponsored hacking group, OilRig, throughout 2022. This covert operation involved the deployment of three distinct malicious software loaders – ODAgent, OilCheck, and OilBooster – each strategically designed to maintain persistent access to targeted organizations in Israel.
Utilization of Microsoft Cloud Services: One of the standout features of OilRig’s arsenal is its adept use of Microsoft cloud services for Command and Control (C2) server communication and data transmission. The group seamlessly integrated the Microsoft Graph API for OneDrive and Outlook, as well as the Microsoft Exchange Web Services (EWS) API. This ingenious tactic effectively conceals the malefactor’s infrastructure by camouflaging it within regular network traffic.
Targeted Sectors: The scope of OilRig’s targets is broad, spanning organizations in healthcare, manufacturing, and local government entities. Notably, these entities had been previously targeted by OilRig, suggesting a sustained interest and persistence in compromising these sectors.
The Arsenal:
- ODAgent: This C#/.NET loader utilizes the Microsoft OneDrive API for C2 server communication. ODAgent empowers attackers to upload and execute payloads while efficiently deleting intermediary files, leaving minimal traces of their activities.
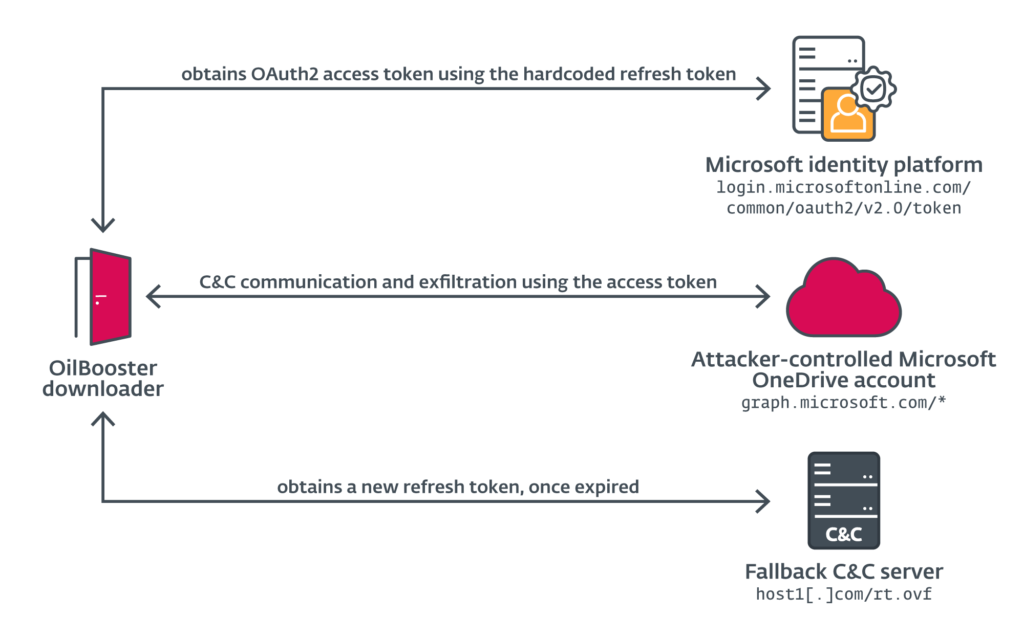
- OilBooster: Similar to ODAgent, OilBooster employs the Microsoft OneDrive API as a C2 server. What sets it apart is the use of the Microsoft Graph API to connect to a Microsoft Office 365 account. This allows for interaction with the attacker’s OneDrive account, facilitating the seamless exchange of commands and payloads from victim-specific folders.
- SampleCheck5000 (SC5k): This updated loader interacts with a shared Microsoft Exchange mail account using the Office Exchange Web Services API. Its primary function is to download and execute additional OilRig tools, showcasing the group’s commitment to maintaining a sophisticated and evolving toolkit.
- OilCheck: Operating similarly to SampleCheck5000, OilCheck extracts commands from draft messages. However, it diverges in its use of the Microsoft Graph API for network communications, adding another layer of complexity to OilRig’s tactics.
Similarities to PowerExchange: Interestingly, the ESET report notes striking resemblances between OilRig’s tools and the PowerExchange group’s backdoor. Both groups leverage email for data transmission, albeit with variations in execution. In PowerExchange’s case, data is sent to the attacker’s email address using the victim organization’s mail server.
Shared Accounts for Communication: A common thread across these instances is the use of a shared account (email or cloud storage) controlled by OilRig for communication with its operators. This shared account is typically accessed by multiple victims, allowing the loaders to download commands, receive additional payloads, and send command results and prepared files.
OilRig’s persistent and stealthy tactics, as outlined in the ESET report, underscore the evolving nature of cyber threats and the need for organizations to remain vigilant. As we delve into 2023, cybersecurity professionals must adapt their strategies to counteract these sophisticated and targeted attacks, emphasizing the importance of robust defense mechanisms and threat intelligence.