The Google Threat Intelligence Group (GTIG) has recently uncovered a sophisticated new malware strain, dubbed LOSTKEYS, deployed by the Russian state-sponsored threat actor COLDRIVER (also known as UNC4057, Star Blizzard, or Callisto). This discovery marks a significant evolution in COLDRIVER’s operational toolkit, which until now was primarily focused on credential phishing and email compromise targeting NATO governments, NGOs, journalists, and former intelligence officers.
Background on COLDRIVER
COLDRIVER has been active for several years, with previous malware campaigns including the 2024 SPICA malware. The group’s modus operandi involves highly targeted phishing attacks aimed at stealing credentials from personal and organizational email accounts. Once inside, they exfiltrate emails, contact lists, and in some cases, deploy malware to gain deeper access to victim systems. Their targets are predominantly Western government advisors, military personnel, think tanks, and individuals connected to Ukraine, supporting Russia’s strategic intelligence objectives.
The LOSTKEYS infection chain: a multi-stage PowerShell attack
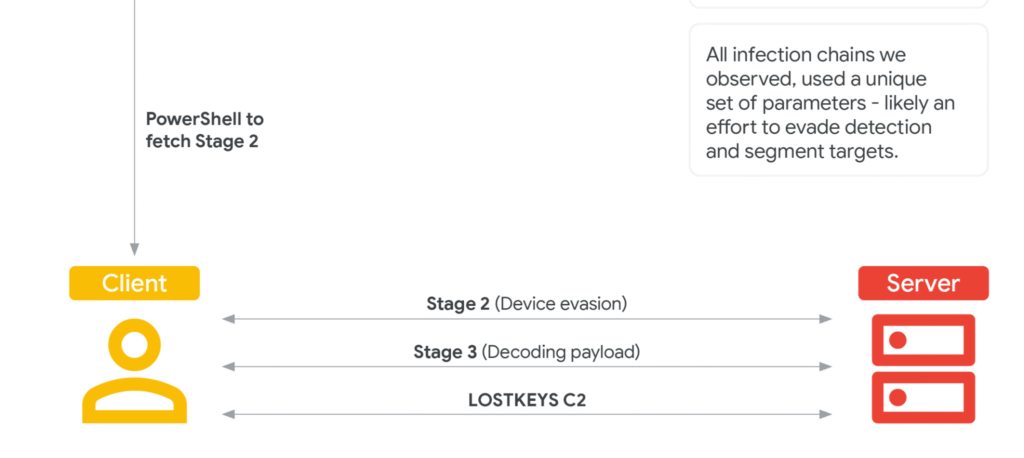
LOSTKEYS is delivered through a multi-stage infection chain that begins with a social engineering tactic involving a fake CAPTCHA on a lure website. Victims are tricked into copying a PowerShell command to their clipboard and running it manually via the Windows “Run” prompt-a technique known as “ClickFix”. This method bypasses many traditional detection mechanisms by relying on user interaction.
- Stage 1: the initial PowerShell script fetches and executes a second-stage payload from a remote server (notably the IP 165.227.148[.]68).
- Stage 2: to evade sandbox and virtual machine analysis, the second stage hashes the device’s display resolution and halts execution if it matches known VM configurations. If cleared, it proceeds to download the third stage.
- Stage 3: this stage downloads a Base64-encoded PowerShell script that pulls down two additional files:
- A Visual Basic Script (VBS) “decoder” responsible for decrypting the final payload.
- An encoded payload blob, which the decoder decrypts using a unique substitution cipher with two keys per infection chain.
Google researchers provided a Python script for decoding the final payload, highlighting the sophistication and custom nature of this malware.
The final payload: LOSTKEYS
The decoded VBS payload, LOSTKEYS, is a versatile espionage tool designed to:
- Steal files from a hard-coded list of file extensions and directories, focusing on documents likely to contain valuable intelligence.
- Collect and exfiltrate detailed system information and running processes to the attacker.
- Operate stealthily, only deployed in highly selective cases where credential theft alone is insufficient.
This malware complements COLDRIVER’s existing capabilities, previously relying on credential theft and selective deployment of SPICA malware for document theft. LOSTKEYS represents a new, more targeted approach to gaining access to sensitive files on compromised machines.
Historical context and uncertain origins
Interestingly, GTIG discovered two additional LOSTKEYS samples dating back to December 2023. These earlier variants masqueraded as Portable Executable (PE) files linked to Maltego software but ultimately executed the same VBS payload. It remains unclear whether these samples were an early iteration by COLDRIVER or repurposed malware from another operation.
Defensive recommendations for high-risk users
Given the targeted nature of COLDRIVER’s campaigns, GTIG strongly recommends:
- Enrolling in Google’s Advanced Protection Program for enhanced account security.
- Enabling Enhanced Safe Browsing in Chrome to block malicious sites.
- Applying the principle of least privilege in enterprise environments to restrict script execution.
- Keeping all devices and software fully updated to mitigate exploitation vectors.
- Educating users to be wary of any site prompting them to run commands outside the browser.
Sharing intelligence and Indicators of Compromise
Google has integrated all identified malicious domains, files, and URLs into its Safe Browsing service to protect users globally. Targeted alerts have been sent to Gmail and Workspace users potentially affected by COLDRIVER activity.
To aid the cybersecurity community, GTIG has published detailed Indicators of Compromise (IOCs) and YARA rules for LOSTKEYS, enabling defenders to detect and respond to this threat more effectively.
The discovery of LOSTKEYS underscores the continuous innovation by nation-state actors like COLDRIVER in evolving their malware capabilities beyond credential theft to direct document exfiltration. This campaign exemplifies a sophisticated blend of social engineering, multi-stage payload delivery, and anti-analysis techniques designed to evade detection and maximize intelligence collection. Security teams defending Western governments, NGOs, and related entities should prioritize awareness and mitigation of this threat vector to safeguard sensitive information.
For detailed technical indicators and YARA rules, refer to the Google Cloud Threat Intelligence blog post dated May 2025.