The Lazarus Group, a notorious North Korean state-sponsored hacking collective, has once again demonstrated its sophistication and audacity with a staggering $1.5 billion cryptocurrency heist targeting Bybit, a major crypto exchange. This incident, now considered the largest crypto theft in history, offers a stark reminder of the evolving threat landscape and the critical importance of robust cybersecurity measures within the digital asset space. Forensic investigations have revealed a complex attack chain that exploited vulnerabilities in Safe{Wallet}, a multisig wallet platform, to compromise Bybit’s Ethereum cold wallet.
The attack vector: compromised developer infrastructure
The attack originated with a breach of a Safe{Wallet} developer’s machine. According to investigations by Sygnia and Verichains, malicious code was injected into a seemingly benign JavaScript file (app.safe.global) on February 19, 2025. This code specifically targeted Bybit’s Ethereum Multisig Cold Wallet. Evidence suggests that the attackers may have compromised Safe{Wallet}’s AWS S3 or CloudFront account/API Key, allowing them to inject the malicious JavaScript.
This highlights a critical vulnerability in the software supply chain. By compromising a developer’s machine, the Lazarus Group was able to insert malicious code directly into a trusted application, effectively bypassing many traditional security controls. This type of attack is particularly dangerous because it leverages trust relationships, making it difficult to detect and prevent.
Exploiting the multisig wallet
The compromised JavaScript code allowed the attackers to manipulate a planned transfer of funds from Bybit’s cold wallet to its hot wallet. By intercepting and altering the smart contract logic and masking the signing interface, the attackers were able to redirect over 400,000 ETH and stETH (worth over $1.5 billion) to an address under their control.
The use of a multisig wallet, which requires multiple signatures to authorize transactions, is generally considered a security best practice. However, this incident demonstrates that even multisig wallets are not immune to sophisticated attacks. In this case, the attackers were able to subvert the multisig process by compromising the signing interface, effectively gaining control of the wallet.
Attribution and tactics
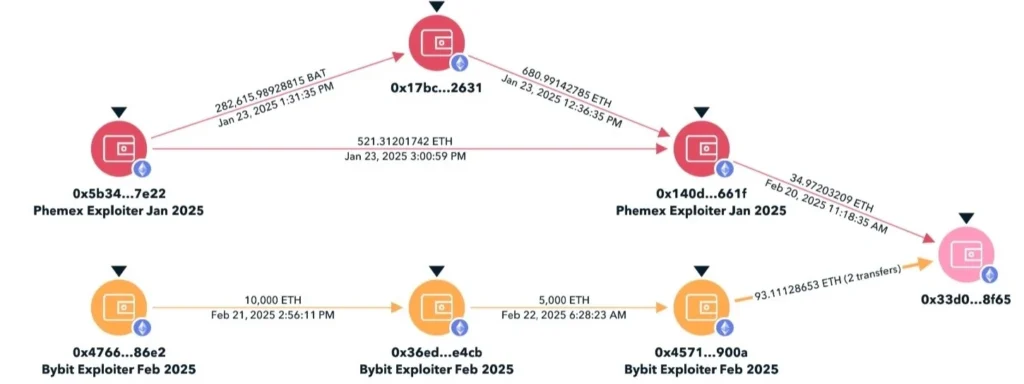
Multiple sources, including crypto fraud investigator ZachXBT, blockchain intelligence company TRM Labs, and blockchain analysis firm Elliptic, have linked the Bybit attack to the Lazarus Group. This attribution is based on the analysis of blockchain transactions, which revealed that some of the stolen funds were sent to Ethereum addresses previously used in other Lazarus-linked crypto heists (Phemex, BingX, and Poloniex).
The Lazarus Group has a long history of targeting the cryptocurrency industry. Chainalysis reported that they stole $1.34 billion in 47 crypto heists in 2024 alone. Elliptic estimates that they have stolen over $6 billion in crypto assets since 2017, with the proceeds allegedly used to fund North Korea’s ballistic missile program.
Their tactics often involve sophisticated social engineering, spear-phishing campaigns, and the exploitation of software vulnerabilities. They are known for their patience, persistence, and ability to adapt to evolving security measures.
Lessons learned and mitigation strategies
The Bybit hack serves as a wake-up call for the cryptocurrency industry. It underscores the need for:
- Enhanced Supply Chain Security: organizations must implement robust security controls to protect their software supply chains, including thorough vetting of third-party vendors, code signing, and regular security audits.
- Endpoint Security: securing developer machines is paramount. This includes implementing strong authentication, access controls, and endpoint detection and response (EDR) solutions.
- Smart Contract Audits: while Safe’s smart contracts themselves were not found to be vulnerable, rigorous smart contract audits are essential to identify and mitigate potential vulnerabilities.
- Transaction Monitoring and Anomaly Detection: implementing real-time transaction monitoring and anomaly detection systems can help identify and respond to suspicious activity.
- Collaboration and Information Sharing: sharing threat intelligence and collaborating with law enforcement and other organizations is crucial to disrupting the activities of groups like Lazarus.
Bybit has taken steps to restore its ETH reserves and has stated that it remains solvent. Safe{Wallet} has rebuilt its infrastructure, rotated credentials, and implemented additional security measures. However, the long-term impact of this incident on the reputation of both companies remains to be seen.
The Lazarus Group’s successful attack on Bybit highlights the ongoing challenges of securing cryptocurrency assets in the face of sophisticated, state-sponsored adversaries. As the cryptocurrency industry continues to grow, it is essential that organizations prioritize cybersecurity and adopt a proactive approach to threat mitigation.