In August 2024, a significant cyber assault orchestrated by the AISURU botnet targeted the distribution platforms of the highly anticipated Chinese game, Black Myth: Wukong. This attack was meticulously planned and executed in four distinct waves, strategically timed to coincide with peak gaming hours across various global time zones. The attackers unleashed sustained Distributed Denial of Service (DDoS) attacks on hundreds of servers belonging to Steam and Perfect World, aiming for maximum disruption and chaos.
Emergence of AIRASHI
Following the initial wave of attacks, the AISURU botnet temporarily paused its operations in September. However, driven by financial incentives, it resurfaced in October under a new guise referred to as kitty. By late November, this botnet evolved further into what is now known as AIRASHI. This latest iteration boasts several alarming features:
- Exploitation of Vulnerabilities: AIRASHI exploits a 0DAY vulnerability found in cnPilot routers, alongside other known vulnerabilities in various devices.
- Enhanced Security Measures: The botnet employs RC4 encryption for sample strings and utilizes HMAC-SHA256 verification combined with ChaCha20 encryption for its command and control (CNC) communications.
- Mocking Security Researchers: The CNC domain names mock security research entities, including XLAB, showcasing a brazen attitude towards cybersecurity efforts.
DDoS capabilities and activities
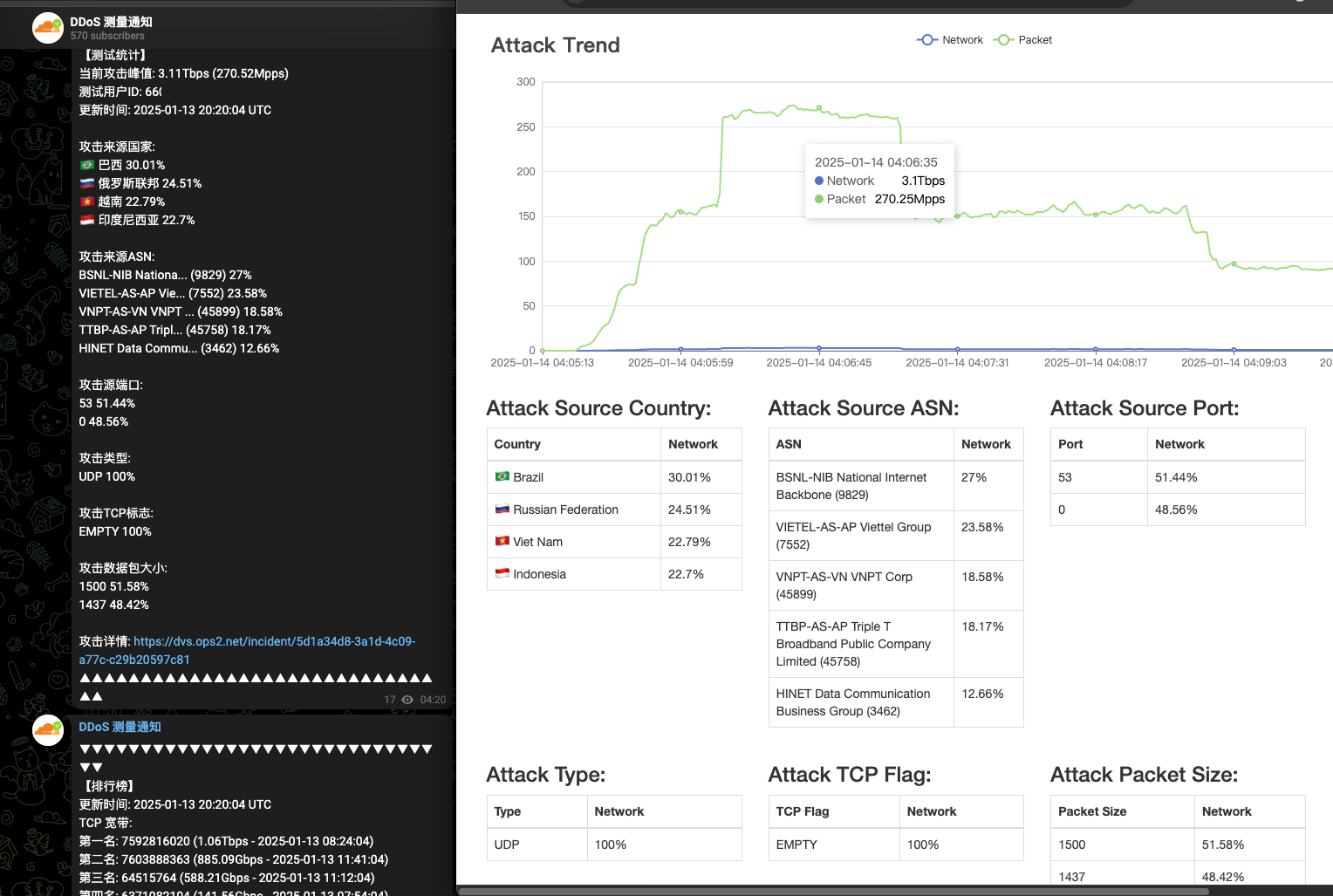
AIRASHI has demonstrated formidable DDoS capabilities, with peak attack traffic recorded at an astonishing 3.11 Tbps. The botnet operators have been actively promoting their attack prowess on platforms like Telegram, where they share statistics from third-party measurement services to intimidate competitors and attract potential clients. The botnet’s targets are diverse, spanning multiple industries and geographical regions including China, the United States, Poland, and Russia. Notably, AIRASHI conducts hundreds of attacks daily without a clear targeting strategy, indicating a broad approach to inflict damage across various sectors.
Technical insights
The AIRASHI botnet is characterized by its modular design with multiple variants. Key features include:
- Sample Variants: AIRASHI-DDoS focuses on DDoS attacks while allowing arbitrary command execution. Other variants like Go-Proxisdk serve as proxy tools.
- Communication Protocols: AIRASHI employs a sophisticated network protocol that integrates HMAC-SHA256 for message integrity and ChaCha20 for encryption.
- Command Structure: The command format has evolved to include new functionalities such as reverse shell access alongside traditional DDoS commands.