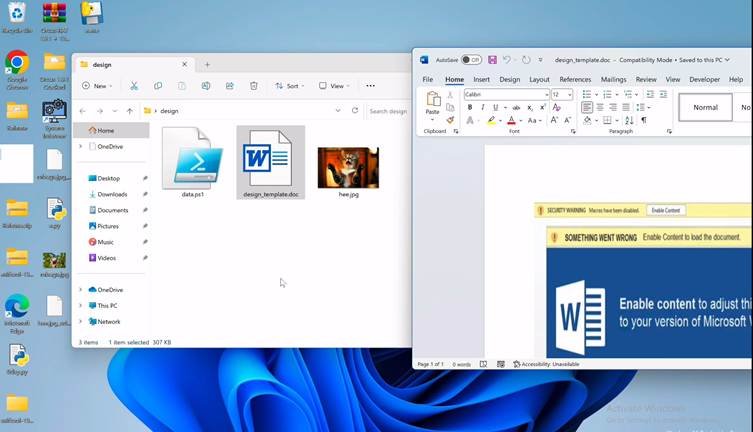
In a concerning development for cybersecurity professionals, threat actors have begun leveraging a novel Fully UnDetectable (FUD) ransomware attack technique that utilizes seemingly benign JPEG image files as the initial infection vector. This sophisticated approach, which has recently surfaced in the wild, is notable for its ability to bypass traditional antivirus (AV) and endpoint detection and response (EDR) solutions, raising the stakes for defenders across all sectors.
Technical breakdown: how the attack works
The core of this new attack methodology lies in the use of steganography and advanced obfuscation. Attackers embed malicious payloads within JPEG images, exploiting the fact that image files are typically considered low-risk by most security solutions. The malware is not simply hidden as an appended executable or script; instead, it is intricately woven into the image data itself, making static and even dynamic analysis challenging.
Upon delivery-often via spear-phishing emails or compromised websites-the infected JPEG is processed by a loader or dropper, which extracts and executes the ransomware payload in memory. This fileless execution further complicates detection, as it leaves minimal forensic artifacts on disk.
Evasion tactics: why traditional defenses fail
Conventional AV engines primarily rely on signature-based detection and heuristic analysis, both of which are circumvented by this technique. The use of steganography means that the malicious code does not match known signatures, and the payload remains dormant until specifically triggered. Additionally, by leveraging legitimate image formats and system processes, the attack chain avoids behaviors typically flagged as suspicious by EDR solutions.
Recent incident reports indicate that even advanced behavioral analytics struggle to identify the attack, as the initial stages mimic normal user or system activity. Only after the ransomware has established persistence and begun encrypting files does its presence become apparent-often too late for effective mitigation.
Implications and recommendations
This evolution in ransomware delivery underscores the urgent need for a multi-layered defense strategy. Experts recommend:
- Deep Content Inspection: deploying tools capable of analyzing image files for embedded code or anomalous structures.
- Memory Analysis: enhancing monitoring of in-memory execution and suspicious process behaviors.
- User Awareness: reinforcing training around the risks of unsolicited attachments, even those appearing as harmless images.
- Threat Intelligence Sharing: collaborating across sectors to rapidly identify and disseminate indicators of compromise (IOCs) related to this attack vector.
The emergence of JPEG-based FUD ransomware represents a significant escalation in adversarial tactics. As attackers continue to innovate, defenders must adopt a proactive, intelligence-driven approach to stay ahead. Continuous research, rapid adaptation of detection methodologies, and cross-industry collaboration will be essential in countering this and future threats.