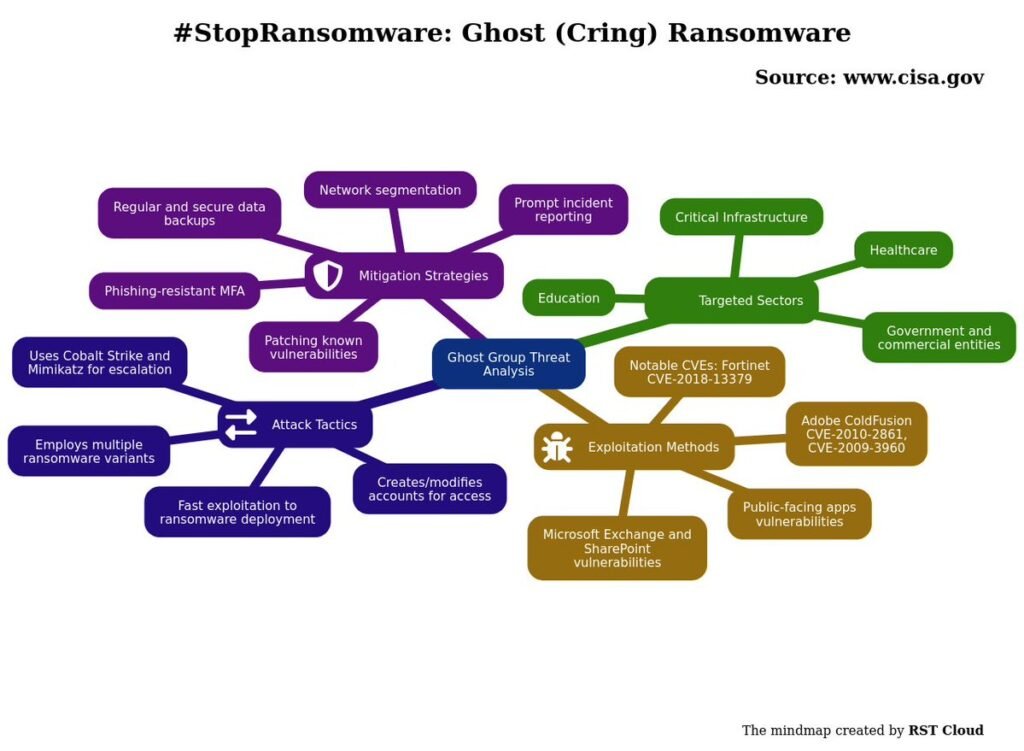
A joint advisory from CISA, the FBI, and the MS-ISAC sheds light on the activities of the Ghost ransomware gang, a cybercriminal group that has been actively targeting organizations across the globe since early 2021. This analysis, pieced together from investigations into numerous cyber incidents, offers valuable insights into Ghost’s methods, motivations, and preferred targets.
Global impact and target diversity
Ghost’s reach is extensive, having compromised entities in over 70 countries, including China, where the gang is believed to be based. Their targets are diverse, spanning critical infrastructure, educational institutions (schools and universities), healthcare providers, government networks, religious organizations, technology and manufacturing firms, and a multitude of small and medium-sized businesses (SMBs). This broad targeting suggests a financially motivated approach, with the gang seeking to maximize their potential pool of victims.
Modus Operandi: exploiting known vulnerabilities
One of the most notable aspects of Ghost’s operations is their reliance on readily available exploits for known vulnerabilities. Instead of developing sophisticated zero-day exploits, they focus on targeting internet-facing services running outdated software or firmware. This “low-hanging fruit” approach allows them to efficiently compromise systems with minimal effort.
Specifically, the advisory highlights Ghost’s exploitation of vulnerabilities in:
- Fortinet FortiOS (CVE-2018-13379)
- Adobe ColdFusion (CVE-2010-2861, CVE-2009-3960)
- Microsoft SharePoint (CVE-2019-0604)
- Microsoft Exchange (CVE-2021-34473, CVE-2021-34523, CVE-2021-31207 – “ProxyShell”)
The fact that Ghost is leveraging vulnerabilities, some of which are over a decade old, underscores the critical importance of patching and maintaining up-to-date software.
Post-Exploitation activities and toolset
Once inside a vulnerable system, Ghost typically deploys web shells and establishes Cobalt Strike beacons for command and control. While they don’t appear to prioritize long-term persistence, they have been observed creating new local and domain accounts and modifying existing passwords.
Cobalt Strike serves as a central tool for privilege escalation, lateral movement, and other malicious activities. The gang also utilizes open-source tools such as “SharpZeroLogon”, “SharpGPPPass”, “BadPotato”, and “GodPotato” to further their objectives. They frequently use Cobalt Strike to enumerate running processes, identify antivirus software, and attempt to disable Microsoft Defender on networked devices. WMIC (Windows Management Instrumentation Command-Line) is used to execute PowerShell commands on other systems, often to deploy additional Cobalt Strike beacons.
Ransom demands and data exfiltration
Ghost’s end goal is financial extortion. They claim to exfiltrate data and threaten to sell it if a ransom is not paid. However, the FBI has observed limited evidence of significant data exfiltration, particularly of intellectual property (IP) or personally identifiable information (PII). While the gang has been known to use Mega.nz for data uploads, the typical data volume is reported to be less than hundreds of gigabytes. This suggests that the threat of data leakage may be more of a scare tactic than a core component of their operations.
Command and Control infrastructure
Ghost relies heavily on Cobalt Strike beacons and team servers for command and control. They often connect directly to IP URIs rather than registering domains for their C2 servers. For communication, they commonly use email services like Tutanota, Skiff, ProtonMail, Onionmail, and Mailfence.
Encryption and anti-forensic techniques
To encrypt victim data, Ghost employs various ransomware payloads, including Cring.exe, Ghost.exe, ElysiumO.exe, and Locker.exe. They also attempt to hinder data recovery efforts by deleting Windows event logs, shadow copies, and disabling the Volume Shadow Copy Service.
Indicators of Compromise (IOCs)
The CISA/FBI advisory includes a list of indicators of compromise (IOCs) that organizations can use to determine if they have been compromised by Ghost. These IOCs are invaluable for proactive threat hunting and incident response.
The Ghost ransomware gang represents a persistent threat to organizations of all sizes and across various sectors. Their reliance on known vulnerabilities highlights the importance of basic cybersecurity hygiene, including regular patching, strong password management, and network segmentation. While they may not be the most sophisticated actors, their widespread targeting and adaptability make them a force to be reckoned with. Organizations should review the CISA/FBI advisory and implement the recommended mitigations to protect themselves from this evolving threat.