In August 2024, FortiGuard Labs unveiled a concerning new player in the cybersecurity landscape: Emansrepo, a Python-based infostealer. This malware has been propagated through cunning phishing emails, often disguised as fake purchase orders and invoices, targeting unsuspecting users. The timeline of Emansrepo’s operations traces back to November 2023, when it began its nefarious activities.
How Emansrepo Operates
Emansrepo is designed to extract sensitive data from its victims. It collects information from web browsers and specific directories, compresses this data into a zip file, and subsequently sends it to the attacker’s email. This method of exfiltration emphasizes the need for users to be vigilant about the data they handle and share online.
One notable development in the Emansrepo saga is its weaponization of HTML files to specifically target Windows users. This evolution demonstrates the malware’s adaptability in exploiting various platforms and technologies. By packaging itself using PyInstaller, Emansrepo can reach non-Python users, further broadening its attack surface. Additionally, attackers utilize crafted links that redirect victims to malicious HTML downloads, increasing the likelihood of successful infections.
The Attack Chain
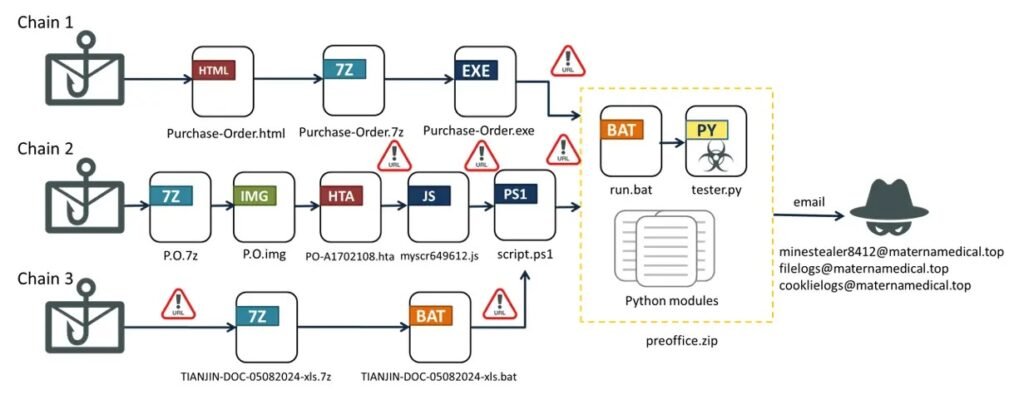
By mid-2024, the attack methodology associated with Emansrepo underwent significant changes. The malware now employs a complex multi-stage dropper that operates through three distinct infection chains.
- Chain 1: Victims are enticed to a fraudulent download page for a 7z archive, which contains an executable named Purchase-Order.exe. This executable retrieves another zip file—preoffice.zip—housing essential Python modules and a malicious script called tester.py.
- Chain 2: An HTA file embedded with JavaScript initiates a PowerShell script (script.ps1) that extracts preoffice.zip and executes Emansrepo via run.bat.
- Chain 3: The final chain involves a BatchShield-obfuscated batch file delivered through phishing emails, which runs script.ps1 in PowerShell to download and execute the malicious script.
The interconnection between these chains underscores the comprehensive strategy employed by Emansrepo to bypass security measures and successfully infiltrate systems.
Phases of Data Exfiltration
Emansrepo operates in three distinct phases:
- Harvesting: It collects user data, including login credentials, credit card information, web history, autofill data, and small text files.
- Extracting: The malware targets PDFs, compresses browser extensions, and captures data from crypto wallets and gaming platforms.
- Exfiltrating: Finally, it extracts browser cookies, utilizing temporary folders for storage and ensuring data is deleted post-exfiltration to avoid detection.
Evolution from Prysmax
Initially, Emansrepo emerged as a variant of Prysmax, with a known hash of e346f6b36569d7b8c52a55403a6b78ae0ed15c0aaae4011490404bdb04ff28e5. However, between November and December 2023, it evolved into a more sophisticated variant (hash: ae2a5a02d0ef173b1d38a26c5a88b796f4ee2e8f36ee00931c468cd496fb2b5a). This transformation reflects the malware’s capacity to adapt and refine its tactics over time.
Connected Campaigns
Compounding the threat is a connected campaign utilizing Remcos—a remote access trojan disseminated through DBatLoader phishing schemes. The presence of such interconnected threats emphasizes the urgent need for robust cybersecurity measures across organizations and individual users alike.
Conclusion
The emergence and evolution of Emansrepo serve as a stark reminder of the ever-changing landscape of cyber threats. With its sophisticated multi-stage attack chains and ability to adapt to various environments, Emansrepo highlights the critical importance of cybersecurity awareness and preparedness. Users must remain vigilant against phishing attempts and adopt strong security practices to safeguard their sensitive information from evolving threats like Emansrepo.