Read Time:1 Minute, 13 Second
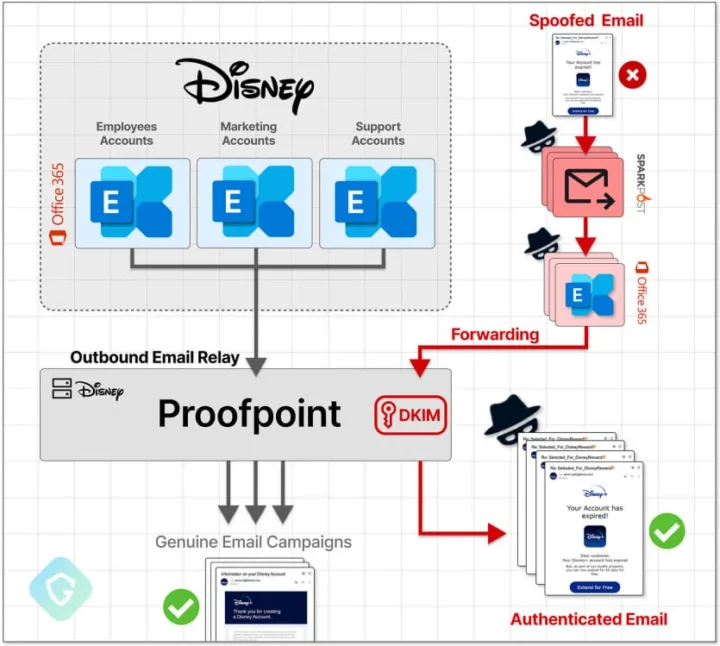
An unknown attacker exploited a vulnerability in Proofpoint’s email routing settings to send mass fraudulent messages impersonating well-known companies such as Best Buy, IBM, Nike, and Walt Disney. The campaign, dubbed EchoSpoofing, began in January and concluded in June, sending up to 14 million emails daily at its peak.
Key Details:
- Exploitation Method: Attackers utilized a configuration error on Proofpoint’s servers, allowing them to modify email routing settings and send emails from any Microsoft 365 tenant through Proofpoint’s infrastructure.
- Authenticity: The fraudulent emails were sent with genuine SPF and DKIM signatures, making them highly convincing and difficult to detect as spoofed.
- Volume: On average, three million emails were sent daily, with a peak of 14 million on one day in June.
- Infrastructure: Emails were routed through Microsoft 365 clients controlled by attackers and relayed through Proofpoint to users of free email services like Yahoo!, Gmail, and GMX.
- Tools: A compromised version of PowerMTA and various IP addresses and VPS were used for mass mailings.
Impact:
- Primary Goal: The campaign aimed to steal funds and credit card information while minimizing detection risk.
- Security Measures: Proofpoint has taken active countermeasures since June. They emphasized that customer data was not compromised and provided recommendations for identifying phishing attempts.
Recommendations:
- For VPS Providers: Limit the ability to send large quantities of messages from their servers.
- For Email Services: Restrict the capabilities of new and unverified users to send mass messages and spoof domains.