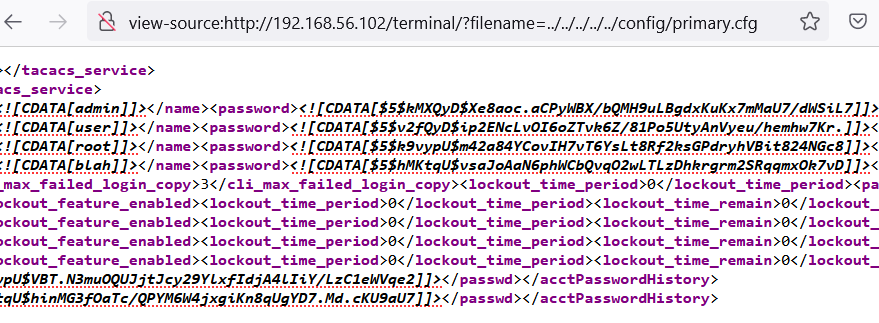
In the realm of cybersecurity, the uncovering of vulnerabilities is a crucial step toward reinforcing the digital fortresses that safeguard our networks. Recently, David Yesland from Rhino Security Labs conducted an external network penetration test, shining a spotlight on the Extreme Operating System (EXOS) used by Extreme Networks. The discoveries made during this assessment unveil a quartet of vulnerabilities that demand immediate attention from organizations relying on EXOS to power their network infrastructure.
CVE-2023-43121: Unauthenticated Root File Read Exposes Password Hashes
The first vulnerability discovered by Yesland poses a severe risk, as it allows unauthenticated users to read root files, thereby exposing password hashes for the device. This flaw creates a potential gateway for catastrophic breaches, providing attackers with access to sensitive information that could unlock the proverbial “keys to the kingdom.”
CVE-2023-43120: Privilege Escalation from Read-Only User to Read-Write Admin
The second vulnerability highlights a critical issue where a read-only user can elevate their privileges to a read-write admin level. This particular weakness effectively opens a backdoor for attackers, granting them extensive control over network devices and the ability to manipulate data and operations at will.
CVE-2023-43118: Cross-Site Request Forgery to Remote Code Execution
The third vulnerability introduces a dangerous pathway from Cross-Site Request Forgery (CSRF) to Remote Code Execution (RCE). This sophisticated attack vector demonstrates how seemingly innocuous web requests can lead to a complete system takeover, posing a significant threat to organizations relying on EXOS.
CVE-2023-43119: Arbitrary File Write as Root via Read-Only User
Arguably the most alarming of the vulnerabilities discovered is the fourth one, enabling arbitrary file writing as root through a read-only user. This vulnerability is akin to providing a guest key access to every room, including the most secure areas of the network.
In response to these critical findings, Extreme Networks has acted swiftly, releasing patches in various versions to address the vulnerabilities. CVE-2023-43121 and CVE-2023-43120 have been fixed in version 22.7.5.1-patch1-6 or later, CVE-2023-43118 in version 31.3.100.20 or later, and CVE-2023-43119 in version 31.7.2.28-patch1-35 or later.
Fortifying EXOS Device Security
To fortify the security of your EXOS devices, Extreme Networks recommends enabling the “Enhanced Security Mode” during installation. This mode not only bolsters configuration security but also mandates the use of custom user passwords, discouraging reliance on default credentials.
In addition to applying patches and enabling enhanced security, organizations are advised to proactively alter default passwords on all deployed devices, irrespective of their perceived importance. Overlooking password changes on seemingly less critical devices can create opportune entry points for attackers.
A final and crucial piece of advice is to refrain from exposing management interfaces to the internet. These interfaces harbor elevated privileges, and unnecessary exposure only serves to expand the potential attack surface.
In conclusion, the discovery and swift remediation of these vulnerabilities underscore the ever-present need for proactive cybersecurity measures. By staying vigilant, applying patches promptly, and adhering to best practices, organizations can ensure the resilience of their network infrastructure against potential threats.