Read Time:1 Minute, 19 Second
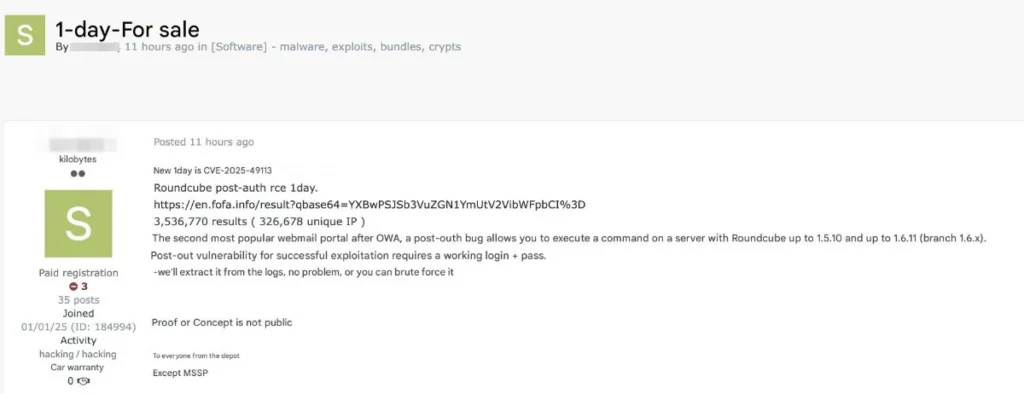
A decade-old Remote Code Execution (RCE) flaw in Roundcube, the widely used open-source email client, has escalated into a global cybersecurity emergency. Designated CVE-2025-49113 with a near-maximum CVSS score of 9.9, the vulnerability allows attackers to execute arbitrary code via unsafe PHP deserialization triggered by unsanitized input parameters.
Key details
- Discovery: The flaw remained undetected for 10 years until a security researcher uncovered it, dubbing it “Email Armageddon” due to its catastrophic potential.
- Patch Timeline: A fix was released on June 1, 2025, but darknet markets began selling exploits within 48 hours.
- Attack Surface: Millions of servers running Roundcube (government agencies, enterprises, and individual users) are at risk.
Why this matters
- Exploit Accessibility: Cybercriminals and APT groups are likely to weaponize this 1-day vulnerability faster than organizations can patch.
- Operational Impact: Unpatched systems could grant attackers full server control, enabling data theft, espionage, or ransomware deployment.
- Global Response: National cybersecurity agencies (e.g., CISA, ENISA) are expected to issue urgent advisories in coming days.
Researcher’s warning
The discoverer emphasized:
“This isn’t just another bug—it’s a skeleton key for email infrastructure. If exploited at scale, it could destabilize global communications.”
Recommendations
- Immediate Action: Apply Roundcube’s June 1 patch (version 1.6.3 or later).
- Monitor Logs: Check for unusual PHP deserialization attempts.
- Threat Intelligence: Track darknet forums for exploit kit updates.
A proof-of-concept video demonstrating the exploit has circulated privately, though researchers urge caution in sharing it publicly.
Stay tuned for updates as this story develops.