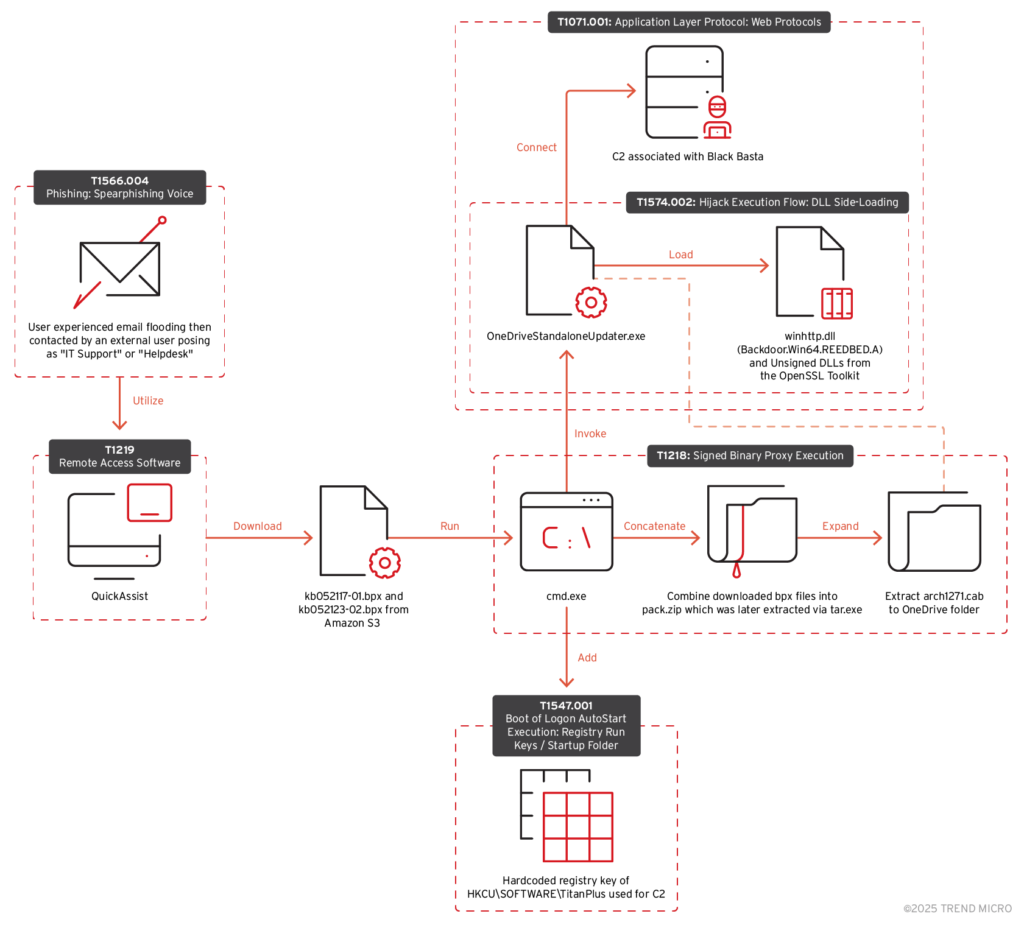
Recent analysis has revealed a significant overlap in the tactics, techniques, and procedures (TTPs) employed by the Black Basta and CACTUS ransomware groups. Specifically, researchers have uncovered that both groups are leveraging the same BackConnect (BC) module to maintain persistent access and control over compromised systems. This convergence1 strongly suggests a potential transition of affiliates from Black Basta to CACTUS.
The BackConnect module: QakBot’s shadow
The BackConnect module, internally tracked as QBACKCONNECT due to its connections to the QakBot loader, provides threat actors with extensive remote control capabilities following initial infiltration. This includes the ability to execute arbitrary commands, facilitating the exfiltration of sensitive data such as login credentials, financial records, and personal files. The module, now being tracked as STAC5777, was initially documented by Walmart’s Cyber Intelligence team and Sophos in late January 2025.
Black Basta’s established TTPs
Over the past year, Black Basta has been observed increasingly using email bombing techniques to deceive targets into installing Quick Assist. Posing as IT support or helpdesk personnel, threat actors guide victims into granting remote access, which is then exploited to sideload a malicious DLL loader (“winhttp.dll”) named REEDBED. This loader, disguised using OneDriveStandaloneUpdater.exe (a legitimate Microsoft OneDrive updater), decrypts and executes the BackConnect module, establishing a persistent foothold within the compromised environment.
CACTUS adopts and expands on Black Basta’s methods
Intriguingly, a recent CACTUS ransomware attack mirrored Black Basta’s modus operandi in deploying the BackConnect module. However, the CACTUS actors extended their operations beyond initial access, implementing additional post-exploitation activities such as lateral movement and data exfiltration. Despite these efforts, the attempted network encryption ultimately failed in the observed instance.
Implications of Black Basta’s internal leaks
The observed overlap in TTPs gains greater significance in light of recent leaks of Black Basta’s internal chat logs, which exposed the group’s inner workings and organizational structure. These leaks revealed the sharing of valid credentials among members, often sourced from information stealer logs. Furthermore, Remote Desktop Protocol (RDP) portals and VPN endpoints were identified as prominent initial access vectors.
A shift in the ransomware landscape?
The shared use of the BackConnect module, coupled with the intelligence gleaned from the Black Basta leaks, points towards a potential shift in the ransomware landscape. The evidence suggests that affiliates with prior experience in Black Basta operations are now contributing to the CACTUS ransomware group, bringing with them established TTPs and expertise. This highlights the fluid nature of the ransomware ecosystem and the need for constant vigilance and adaptation in defensive strategies. Organizations should be aware of these evolving TTPs, including vishing, the abuse of legitimate remote tools like Quick Assist, and the deployment of BackConnect modules, to effectively mitigate the risk of both Black Basta and CACTUS ransomware attacks.