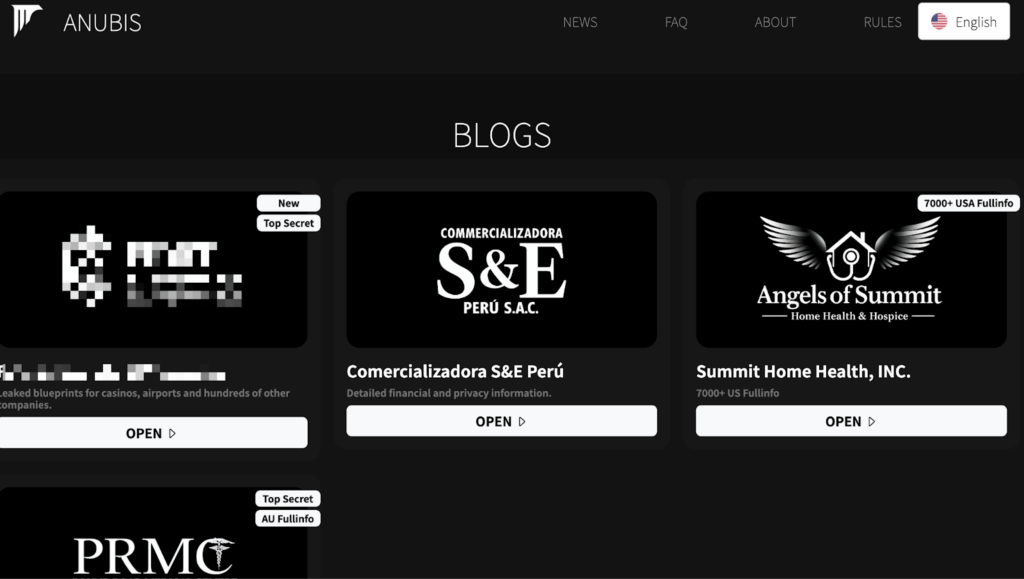
A new player has emerged in the ransomware landscape: Anubis. This group, first observed in December 2024, is quickly making a name for itself through a multi-faceted extortion model that goes beyond traditional ransomware-as-a-service (RaaS). This analysis will explore Anubis’s business model, tactics, and potential impact based on recent observations.
An evolving business model
Anubis distinguishes itself by employing a multi-pronged monetization strategy. While offering a standard RaaS program with an 80/20 revenue share, they also operate data ransom and access monetization affiliate programs. This diversified approach allows affiliates to leverage various attack vectors, maximizing their potential profits.
- Ransomware-as-a-Service (RaaS): Anubis offers a “classic” RaaS model with an 80% ransom share, boasting capabilities targeting Windows, Linux, NAS, and ESXi environments. They also claim privilege escalation and self-propagation features, managed through a web panel.
- Data Ransom: Anubis allows cybercriminals to monetize already stolen data in exchange for 60% revenue. The data must be exclusive, recent (less than six months old), and considered interesting for publication.
- Access Monetization: Anubis offers a 50/50 revenue share for initial access brokers (IABs) providing corporate access credentials. They focus on victims in the US, Europe, Canada, or Australia, excluding educational, governmental, and non-profit sectors.
Tactics and techniques
Anubis employs a range of tactics to pressure victims, including:
- Investigative Articles: Anubis researches victims to create detailed “investigative articles” based on stolen data. These articles are initially published in hidden mode on their blog and used as leverage during negotiations.
- Non-Standard Methods: Anubis threatens victims with “non-standard methods” to increase pressure.
- Third-Party Notification: Anubis threatens to inform affected entities, regulatory bodies (GDPR, EDPB, HHS, etc.), and clients about the data breach.
- Data Leaks: If negotiations fail, Anubis publishes the stolen data for free download on their blog.
Victimology and targeting
Based on early observations, Anubis appears to be opportunistic, but with a potential focus on the healthcare sector. Two of their first four claimed victims were healthcare organizations in Australia and Canada. They also claimed victims in the engineering and construction sectors in Peru and the USA.
Potential implications
Anubis’s emergence poses a significant risk to organizations due to its well-organized structure, diverse monetization methods, and apparent expertise in ransomware operations and data extortion tactics. Their willingness to target critical industries like healthcare raises concerns about the potential for severe disruptions and harm.
Attribution and origins
While definitive attribution remains unclear, several clues suggest the operators may have prior experience in the ransomware or data extortion space. Their posts on forums are written in Russian.
Recommendations
Organizations should take proactive measures to mitigate the risk of Anubis attacks, including:
- Enhanced Security Posture: Implement robust security controls, including multi-factor authentication, intrusion detection systems, and regular security audits.
- Data Backup and Recovery: Maintain up-to-date backups of critical data and ensure a reliable recovery process.
- Incident Response Plan: Develop and regularly test an incident response plan to effectively respond to ransomware attacks and data breaches.
- Employee Training: Educate employees about phishing scams, social engineering tactics, and other common attack vectors.
- Supply Chain Security: Assess the security posture of third-party vendors and partners to mitigate supply chain risks.