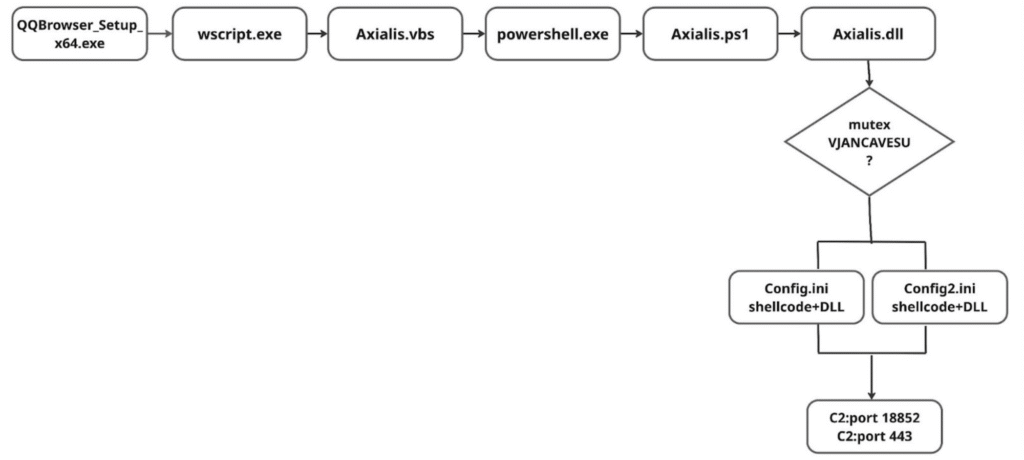
The Winos 4.0 campaign, as dissected by Rapid7, exemplifies the evolving sophistication of contemporary malware operations targeting Chinese-speaking environments. This campaign leverages a multi-layered loader architecture, dubbed the Catena loader, to deliver a stealthy, memory-resident malware that is notably challenging for traditional security tools to detect.
Abuse of NSIS installers and Multi-Stage loading
At the heart of the campaign is the abuse of NSIS (Nullsoft Scriptable Install System) installers, which are trojanized to masquerade as legitimate applications such as QQBrowser, LetsVPN, Telegram, or Chrome. These installers bundle both decoy software (often signed and functional) and a chain of malicious components, including:
- Embedded shellcode in
.inifiles - Malicious DLLs
- PowerShell and VBScript loaders
- Configuration files that double as shellcode containers
This modular approach, where each component is responsible for a discrete stage in the infection chain, allows the attackers to adapt quickly and evade detection.
Reflective DLL injection and sRDI shellcode
A standout technical feature is the use of Shellcode Reflective DLL Injection (sRDI). The shellcode, embedded within binary .ini files, is loaded and executed entirely in memory using custom loaders (e.g., insttect.exe or intel.dll). This technique enables the malware to avoid writing its payloads to disk, drastically reducing its forensic footprint and bypassing many endpoint protection solutions.
The sRDI loader self-parses the shellcode blob, reflectively loads the embedded DLL, and executes its exported function (consistently named VFPower across samples). API calls are resolved dynamically via hashed function names, further complicating static analysis and signature-based detection.
Persistence and evasion techniques
Persistence is achieved through several redundant mechanisms:
- Scheduled tasks registered via dropped PowerShell scripts and XML configuration files
- Process monitoring via batch scripts that relaunch malware components if terminated
- Use of LOLBins (Living Off the Land Binaries) such as
regsvr32.exeto invoke malicious DLLs, blending malicious activity with legitimate system operations
The malware also attempts to disable or evade Microsoft Defender by programmatically adding exclusions for all system drives. Additionally, it checks for the presence of Chinese antivirus products (e.g., 360 Total Security) and includes logic to detect Chinese language settings, indicating a regional targeting focus—though this language check is not strictly enforced in current variants.
Command and Control (C2) infrastructure
Winos 4.0 establishes outbound connections to attacker-controlled servers, primarily hosted in Hong Kong, over both TCP (port 18856) and HTTPS (port 443). The infrastructure and communication ports have remained consistent across observed samples, suggesting a single, persistent threat actor behind the campaign.
Campaign evolution and threat actor adaptability
Since its initial discovery in early 2025, the campaign has shown clear signs of tactical evolution:
- Early variants relied on PowerShell scripts for payload execution, while later samples shifted to direct DLL invocation via
regsvr32.exeto reduce reliance on PowerShell and evade detection. - The infection chain remains modular, allowing the attackers to swap out components, adjust persistence logic, and refine delivery methods in response to security controls and detection efforts.
This adaptability, combined with the use of signed decoy applications and region-specific targeting, points to a well-resourced and technically capable threat group with a long-term operational outlook.
The Winos 4.0 campaign is a textbook example of modern, in-memory malware leveraging layered loaders, reflective DLL injection, and LOLBins to achieve stealth, persistence, and adaptability. Its focus on Chinese-speaking environments, use of legitimate software as cover, and rapid evolution in response to detection underscore the need for advanced behavioral analytics and proactive threat hunting to counter such threats.
“Catena uses embedded shellcode and configuration switching logic to stage payloads like Winos v4.0 entirely in memory, evading traditional antivirus tools
— Rapid7, 2025
Security professionals should monitor for unusual NSIS installer activity, reflective DLL loading, and suspicious scheduled tasks, particularly those invoking regsvr32.exe or referencing seemingly benign .ini files. Continuous intelligence sharing and adaptive detection strategies remain paramount in defending against such sophisticated campaigns.