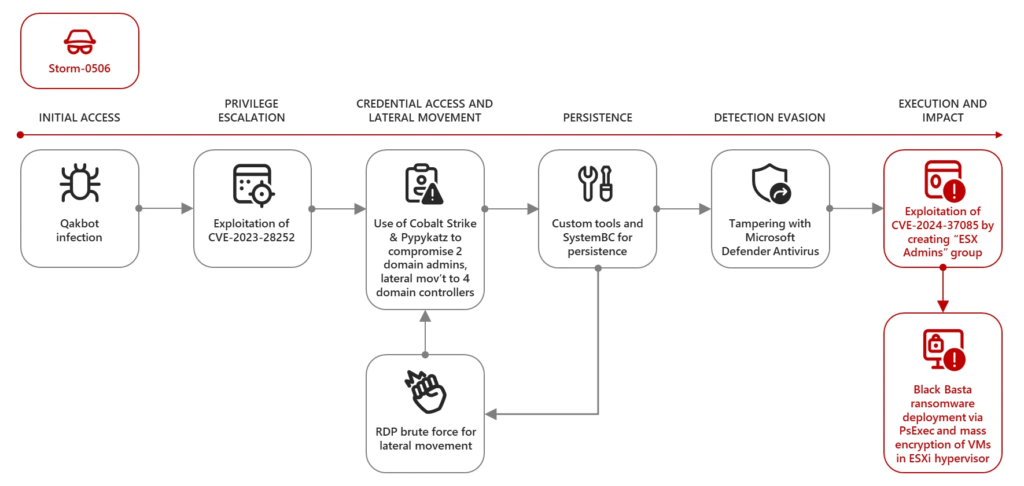
A vulnerability in VMware’s ESXi virtualization platform, identified as CVE-2024-37085, continues to leave thousands of servers susceptible to ransomware attacks. Despite ongoing exploitation by cybercriminals and warnings from major security organizations, 20,275 ESXi instances remain exposed, as discovered by researchers from the Shadowserver Foundation. This medium-severity authentication bypass flaw allows attackers to gain full administrative control of affected systems, leading to potential ransomware attacks and data theft.
Microsoft has reported multiple ransomware gangs actively exploiting this vulnerability to escalate their attacks on domain-joined hypervisors, stealing sensitive data, infiltrating networks, and encrypting critical files. The widespread use of VMware ESXi in enterprise data centers heightens the risk, as a successful breach can disrupt operations and compromise numerous virtual machines hosted on the compromised hypervisor.
Broadcom has released a patch for CVE-2024-37085, and it is imperative that organizations apply it immediately. For those unable to patch promptly, VMware has recommended mitigation steps, including disabling local user accounts and adjusting Active Directory permissions. The Cybersecurity and Infrastructure Security Agency (CISA) has also mandated that U.S. Federal Civilian Executive Branch (FCEB) agencies address this vulnerability urgently due to the ongoing ransomware threats.
Shadowserver’s findings highlight a significant number of potentially vulnerable instances globally, with France, the United States, and Germany having the highest counts. The foundation clarified that their detection is based on remote version checks for patch status, without verifying workarounds or exploitability preconditions.
Organizations relying on VMware ESXi must prioritize patching this vulnerability and implement robust security measures to safeguard their virtualized environments from the escalating threat of ransomware attacks.