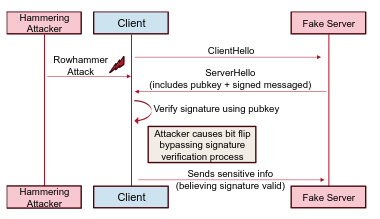
In the ever-evolving landscape of cybersecurity, researchers have unearthed a groundbreaking threat that strikes at the core of computing systems. Dubbed “Mayhem,” this sophisticated attack technique exploits the Rowhammer effect to target the heart of a computer’s memory—CPU internals and stack variables. Mayhem represents a significant leap forward in cyber threats, showcasing the ability to manipulate a system’s memory, corrupting stack and register variables with unprecedented precision.
The Rowhammer Effect: Unraveling Mayhem’s Intricacies
Mayhem’s foundation lies in the Rowhammer effect, a phenomenon where rapid access to a Dynamic Random-Access Memory (DRAM) row induces bit flips in adjacent rows. The ingenious twist comes in how Mayhem manipulates these bit flips, specifically targeting stack variables and register values within a process. By focusing on register values stored in a process’s stack, Mayhem gains the ability to corrupt these values, which, when flushed out to memory, become susceptible to Rowhammer attacks. Upon reloading, the corrupted values wreak havoc, compromising the integrity of the entire process.
Mayhem in Action: A Threat to Critical Data Areas
The methodology behind Mayhem is both intricate and alarming. This attack injects faults into a system’s critical data areas by exploiting the Rowhammer effect. The consequences are far-reaching, with the potential to bypass security protocols, leading to unauthorized access or control over sensitive systems and data.
Researchers demonstrated Mayhem’s capabilities through high-impact scenarios, including bypassing SUDO and SSH authentication and targeting OpenSSL security checks stored in the stack. This novel approach to exploiting Rowhammer extends the attack surface beyond previously known vulnerabilities, raising critical concerns about the security of current systems and highlighting the urgent need for more robust protection mechanisms.
CVE-2023-42465: SUDO Vulnerability and Mitigation
Researchers issued CVE-2023-42465 for a critical flaw found in SUDO up to version 1.9.14. The vulnerability allows Mayhem to manipulate bits in the authentication process, potentially leading to mis-authentication. Engineer Todd C. Miller has submitted a commit to address the CVE-2023-42465 bug, underscoring the need for swift action and mitigation strategies.
The Evolving Nature of Cybersecurity Threats
Mayhem serves as a stark reminder of the constantly evolving nature of cybersecurity threats. As we delve deeper into the digital age, there is an urgent call for a reassessment of existing defense mechanisms and a renewed focus on innovative strategies to safeguard against such sophisticated attacks. The importance of staying ahead in the cybersecurity arms race becomes ever more critical in the face of emerging threats like Mayhem.
Conclusion: A Call to Arms in the Cybersecurity Landscape
In conclusion, the revelation of Mayhem marks a paradigm shift in cybersecurity threats. Its ability to manipulate the core elements of computing systems showcases the need for constant vigilance and adaptation in the face of evolving risks. As the digital age advances, the cybersecurity community must unite in a collective effort to stay one step ahead, ensuring the resilience of our systems against the ever-growing sophistication of threats like Mayhem.