Calisto, a cyberespionage campaign attributed to the Russian FSB’s Center 18 for Information Security (military unit 64829), has been making waves in the cybersecurity community. This group has established itself as a persistent threat against Western institutions with their sophisticated phishing operations and intricate use of social engineering tactics, specifically targeting NATO research entities and strategic organizations.
The Calisto attack strategy centers on leveraging the ClickFix methodology. This tactic employs meticulously crafted spear-phishing emails that impersonate trusted contacts to lure victims into taking actions that compromise security. These campaigns are often disguised as regular correspondence, utilizing decoys like missing attachments or broken PDFs in an attempt to trick users into requesting resends.
Once the user falls victim to the ploy, attackers use carefully curated redirection tactics to deliver their payload. This multi-stage approach increases credibility and maintains operational security. The technical infrastructure behind these attacks provides a clear picture of the sophisticated attack chains at play:
- Phishing Redirectors: Calisto utilizes PHP scripts deployed on compromised servers to redirect users to malicious websites using token parameters through GET requests resembling standard tracking codes.
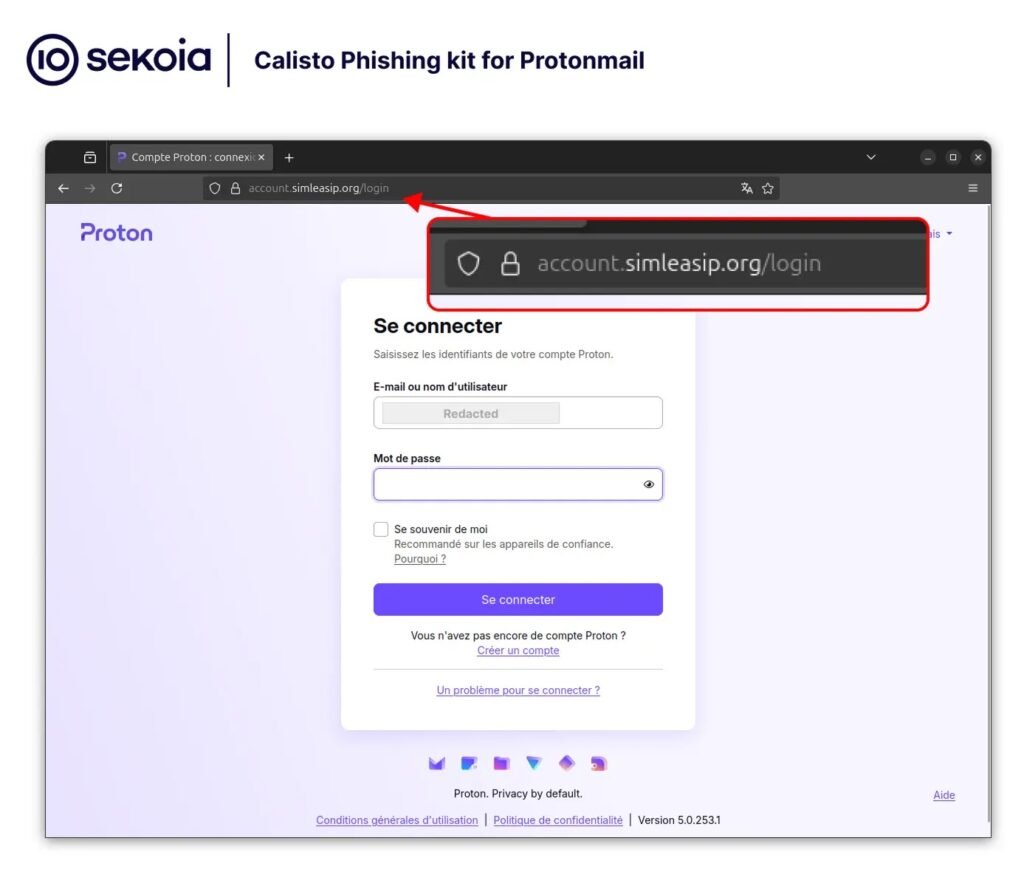
- Credential Harvesting: Once the user clicks, a custom phishing kit hosted on account.simpleasip[.]org, specifically targets ProtonMail accounts through an Adversary-in-the-Middle technique. This kit injects malicious JavaScript into the browser that keeps the cursor focused on password fields every 250 milliseconds, preventing users from navigating away from entering credentials.
The infected user’s entered credentials are then relayed to the attacker’s control server via a custom API hosted at scorelikelygateway.simLeasip[.]org. To maintain the illusion of legitimacy, this process involves presenting legitimate-appearing CAPTCHA and two-factor authentication prompts.
Persistence Through Evolution:
Once Calisto establishes a foothold on a target system, it utilizes several tactics to persist within its environment:
- Domain Registration: The group registers domains using multiple registrars, initially using Regway before transitioning to Namecheap’s free and standard authoritative servers. This allows threat intelligence analysts to track and correlate attack campaigns with medium confidence.
- Proxy Services: Logs reveal extensive use of proxy services, with IP address 196.44.117[.]196 associated with the Big Mama Proxy service, which helps them maintain anonymity and evade detection.
Targeted Attacks:
Despite extensive public disclosures, Calisto continues expanding its phishing operations targeting Ukraine supporters. Organizations involved in humanitarian work, press freedom advocacy, and strategic research remain primary targets aligned with Russian intelligence priorities.
