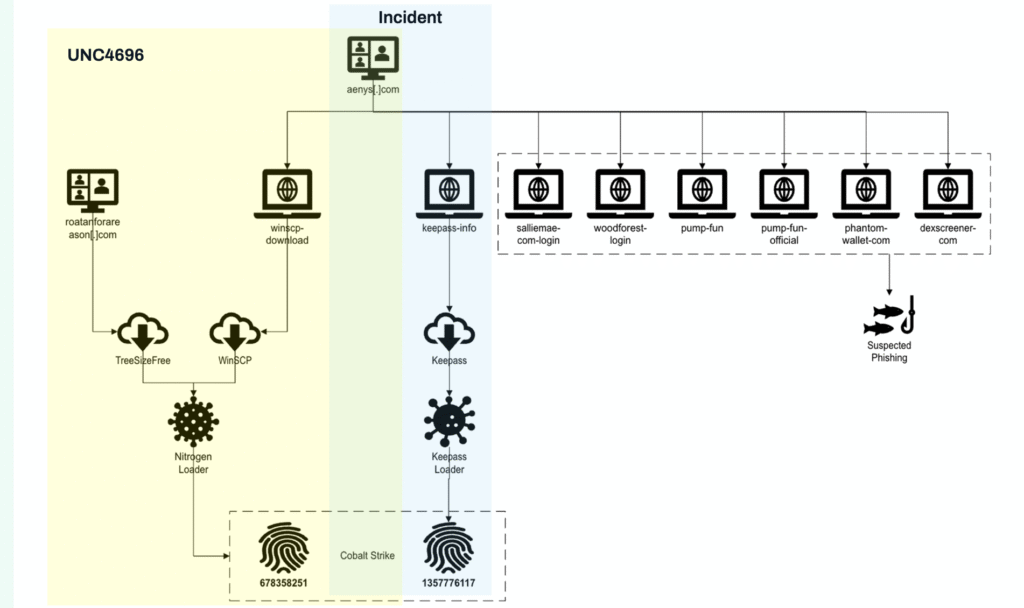
A recent investigation by WithSecure’s Threat Intelligence team has uncovered a sophisticated malware campaign leveraging a trojanized version of the open-source password manager KeePass. This operation, active for at least eight months, marks a significant evolution in post-exploitation tactics, combining credential theft with advanced loader capabilities and ransomware deployment. The campaign has targeted multiple organizations, particularly in Europe, and is linked to a prolific Initial Access Broker (IAB) with a history of high-profile ransomware incidents1.
Campaign overview and initial access
The campaign’s initial access vector was malvertising: attackers registered lookalike KeePass domains and purchased search engine advertisements, effectively redirecting users seeking to download KeePass to malicious sites. The trojanized installer, KeePass-2.56-Setup.exe, was signed with a valid certificate mimicking the legitimate software’s signature, enhancing its credibility and bypassing many security controls1.
Technical analysis: KeeLoader
The modified KeePass installer, dubbed “KeeLoader,” is notable for its dual functionality:
- Malware loader: KeeLoader acts as a loader for Cobalt Strike beacons. Upon installation, it drops modified versions of KeePass.exe and ShInstUtil.exe into the user’s local application data directory. The installer sets up a persistence mechanism by creating an autorun registry key (“keepass”) to launch the malicious ShInstUtil.exe with a specific parameter, which is not present in legitimate versions1.
- Credential theft: the malicious KeePass executable is engineered to export credentials-account names, login details, passwords, associated websites, and comments-into CSV files with randomized names. While the sample analyzed did not automate exfiltration, the deployed Cobalt Strike beacon enables remote retrieval of these files by the attacker1.
The Cobalt Strike payload is stored as an encrypted file (db.idx) masquerading as a JPG, decrypted and executed in-memory using a custom RC4 implementation. The loader’s execution flow leverages the EnumFontsW callback to initiate shellcode execution, demonstrating a sophisticated approach to defense evasion and in-memory payload delivery1.
MITRE ATT&CK mapping and TTPs
The campaign’s tactics, techniques, and procedures (TTPs) span the full cyber kill chain:
- Resource development: registration of lookalike domains and use of malvertising (T1583.001, T1583.008).
- Initial access: drive-by compromise via malicious ads (T1189).
- Execution & persistence: user execution of the trojanized installer, creation of persistent autorun registry keys, and abuse of Windows services (T1204.002, T1547.001, T1543.003).
- Credential access: exfiltration of KeePass database files (T1555.005).
- Lateral movement: use of stolen credentials for RDP, SMB, and SSH access (T1021.001, T1021.002, T1021.004).
- Command and Control: HTTPS-based C2 communications (T1071.001).
- Impact: ransomware deployment, data encryption, and system shutdowns (T1486, T1529)1.
Attribution and criminal ecosystem
Infrastructure analysis links the campaign to a well-established IAB, suggesting a broader ecosystem of ransomware affiliates and “as-a-service” criminal models. The use of trusted code-signing certificates and the modification of open-source software at the source code level represent a notable escalation in attacker investment and operational security1.
Detection and Response Challenges
KeeLoader’s use of valid digital signatures and deep integration with legitimate software routines allowed it to evade most off-the-shelf detection products. Attribution remains challenging due to the modular, service-based nature of the criminal ecosystem and the lack of unique, actor-specific artifacts1.
This campaign underscores the risks associated with supply chain attacks on open-source software and highlights the need for rigorous software provenance checks, enhanced endpoint monitoring, and continuous threat intelligence sharing. The observed techniques-particularly the combination of credential theft and loader functionality in a single, trojanized open-source utility-set a new precedent for post-exploitation tradecraft in ransomware operations.