A new Android spyware, dubbed “KoSpy,” has been discovered by researchers at Lookout, adding another concerning tool to the arsenal of North Korean threat actors. This spyware, attributed with medium confidence to the APT37 group (also known as ScarCruft), demonstrates a persistent and evolving threat targeting Korean and English-speaking users. Let’s delve into the details of KoSpy, its capabilities, and the implications for mobile security.
KoSpy: A Deep Dive into the Spyware’s Functionality
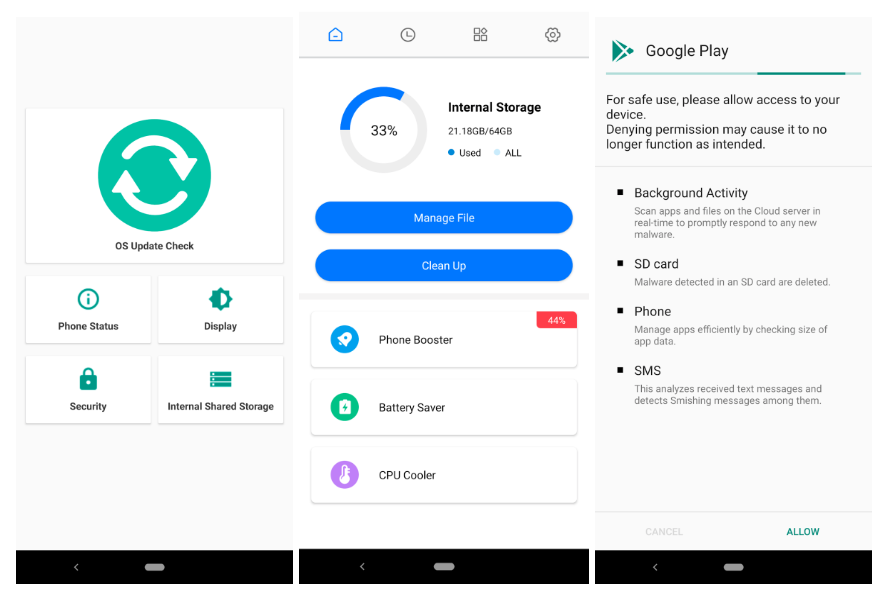
First observed in March 2022, KoSpy continues to be actively deployed, with new samples detected as recently as March 2024. What makes this spyware particularly insidious is its use of social engineering to masquerade as legitimate utility applications. These include:
- “File Manager”
- “Software Update Utility”
- “Kakao Security”
- “Phone Manager”
- “Smart Manager”
These deceptive apps, some of which were even available on the Google Play Store, present a basic, often functional, interface to avoid arousing suspicion. However, behind the facade, KoSpy initiates its malicious activities.
Two-Stage C2 Infrastructure
KoSpy employs a sophisticated two-stage command-and-control (C2) infrastructure. The initial configuration, including an on/off switch and the C2 server address, is retrieved from a Firebase cloud database. This approach provides the attackers with flexibility and resilience, allowing them to quickly disable the spyware or change the C2 server if necessary.
After retrieving the C2 address, KoSpy checks to ensure it is running on a real device and verifies that the current date is past a hardcoded activation date, likely to avoid premature detection.
Once active, KoSpy can collect a wide range of sensitive information from infected devices, including:
- SMS messages
- Call logs
- Device location
- Files and folders on local storage
- Audio recordings and camera snapshots
- Screenshots and screen recordings
- Keystrokes (via accessibility services abuse)
- Wi-Fi network details
- List of installed applications
This data is then encrypted with a hardcoded AES key and transmitted to the C2 servers. The use of dynamically loaded plugins enables KoSpy to adapt and expand its functionality on the fly.
Targeting and distribution vectors
Researchers believe that KoSpy is primarily targeted at Korean and English-speaking users. This is supported by the fact that many of the fake applications have Korean language titles and the UI supports both Korean and English.
The distribution methods are particularly concerning. While some samples were found on third-party app stores like Apkpure, others were available on the Google Play Store, highlighting the challenges in preventing malicious apps from infiltrating official channels.
The Lookout Threat Lab’s investigation revealed connections between KoSpy and previous malicious activities attributed to North Korean APT groups APT43 (Kimsuky) and APT37. Specifically, one of KoSpy’s C2 domains, st0746[.]net, resolves to an IP address that has been linked to other malicious domains targeting Korean users, including those associated with the Konni Windows RAT (linked to APT37) and infrastructure used by Thallium (APT43).
These overlaps in infrastructure, targeting, and tactics make definitive attribution challenging, but based on the evidence, Lookout assesses with medium confidence that KoSpy is the work of APT37.
Implications for cybersecurity professionals
The discovery of KoSpy underscores the ongoing threat posed by North Korean APT groups and the importance of proactive mobile security measures. Here are key takeaways for cybersecurity professionals:
- Mobile devices are a prime target: organizations must recognize that mobile devices are increasingly targeted by sophisticated threat actors.
- Employee education is crucial: users need to be educated about the risks of downloading apps from unofficial sources and the importance of scrutinizing permissions.
- Mobile threat detection solutions are essential: implementing mobile threat detection (MTD) solutions can help identify and prevent the installation of malicious apps like KoSpy.
- Stay informed about emerging threats: continuously monitoring threat intelligence feeds and security research is vital to stay ahead of evolving threats.
KoSpy serves as a stark reminder of the ever-present need for vigilance and robust security practices in the face of persistent and adaptable adversaries.