Cato Networks has uncovered a sophisticated IoT botnet, dubbed Ballista, targeting TP-Link Archer routers by exploiting a two-year-old vulnerability (CVE-2023-1389). This threat, linked to an Italian threat actor, underscores the persistent risks posed by unpatched IoT devices and the evolving tactics of cybercriminals. Here’s what security teams need to know.
Ballista’s origins and targets
Ballista’s name draws inspiration from the Roman empire’s missile launcher, reflecting both its destructive potential and its suspected Italian origins. While attribution remains at “moderate confidence,” Cato Networks identified ties to Italy through IP addresses and malware binary strings.
Since its first detection in January 2025, Ballista has primarily targeted organizations in the U.S., Australia, China, and Mexico, with victims spanning manufacturing, healthcare, technology, and services sectors. The botnet remains active as of mid-February 2025.
Exploiting CVE-2023-1389: a recurring weakness
The botnet capitalizes on CVE-2023-1389, a TP-Link Archer router vulnerability first exploited in May 2023 after its discovery at Pwn2Own 2022. This flaw allows unauthorized command execution via manipulated country parameters in router APIs. Despite patches being available for years, over 6,000 internet-exposed devices remain vulnerable, according to Censys.
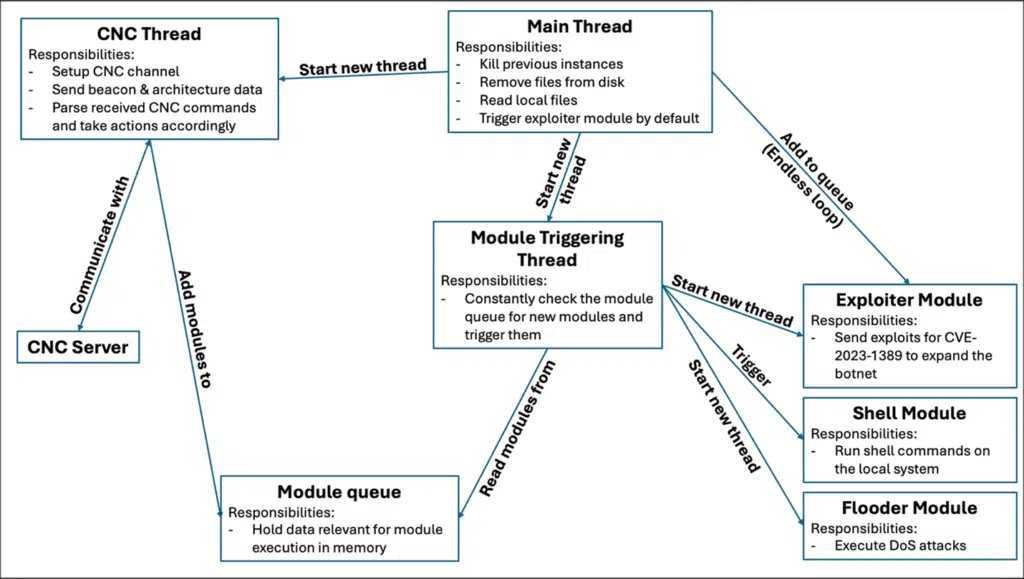
Ballista’s initial payload is a dropper that downloads malware to compromised routers. Once installed, it establishes a TLS-encrypted C2 channel on port 82, enabling full device control.
Capabilities and evolution
Ballista’s malware toolkit includes:
- Self-removal to evade detection.
- Configuration file extraction for lateral movement.
- DDoS attack execution (HTTP/S, TCP, UDP floods).
- Shell command execution for further exploitation.
Notably, Cato observed attackers transitioning from hardcoded IP addresses to Tor-based C2 domains, a shift likely designed to complicate tracking and takedowns.
Broader implications for IoT security
Ballista joins a growing list of botnets (e.g., Eleven11bot, BadBox) weaponizing unpatched IoT devices. Its emergence highlights three critical trends:
- Legacy vulnerabilities remain lucrative: Attackers prioritize low-hanging fruit, especially in under-secured IoT ecosystems.
- Geopolitical nuances in attribution: Moderately confident links to Italian actors suggest possible regional threat actor diversification.
- Defensive evasion via Tor: The move to Tor emphasizes attackers’ focus on operational resilience.
Mitigation strategies
- Patch TP-Link Archer routers: Ensure CVE-2023-1389 is remediated (firmware updates).
- Monitor port 82 traffic: Unusual TLS activity on this port may indicate compromise.
- Segment IoT devices: Isolate critical infrastructure from vulnerable endpoints.
- Leverage threat intelligence: Track IoCs (IPs, Tor domains) associated with Ballista.
The Bottom Line
Ballista exemplifies how attackers continue to exploit outdated IoT vulnerabilities while refining tradecraft to evade detection. For organizations, proactive patching, network monitoring, and robust segmentation are non-negotiable defenses in an era where ancient Roman warfare tactics meet modern cybercrime.