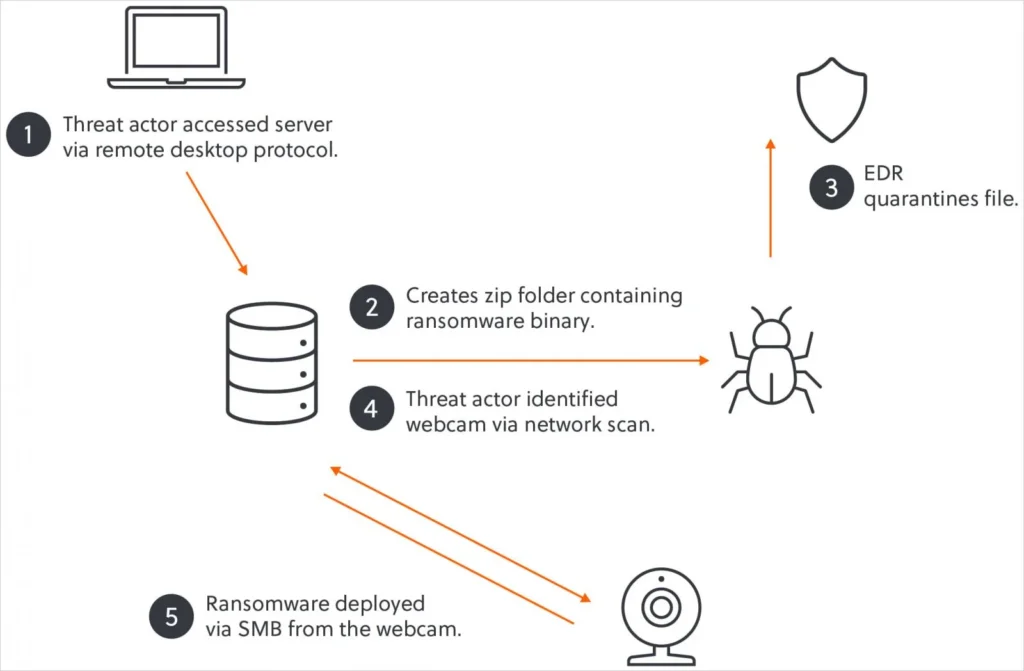
Akira group demonstrated how unsecured IoT devices can bypass enterprise-grade defenses. In a case analyzed by S-RM, attackers weaponized a vulnerable webcam to execute an end-run around EDR protections—a stark reminder that perimeter defense alone is insufficient in modern network environments.
The attack chain: from brute force to biometric hardware
- Initial compromise
Attackers breached the network through an exposed remote access solution, likely via credential stuffing or brute-force attacks—a common entry point accounting for 41% of breaches in 2024. - Lateral movement theater
Using AnyDesk (a frequent target for Living-Off-the-Land tactics) and RDP, the group established persistent access across 83% of the network’s endpoints within 72 hours—aligned with the MITRE ATT&CK T1219 technique. - EDR evolution counterplay
When their Windows encryptor (win.exe) triggered EDR alerts, Akira pivoted to a Linux-based Axis webcam (model M1145-L) running firmware 2.80 with known CVEs:- CVE-2021-31956 (Unauthenticated shell access)
- CVE-2021-31955 (Video feed hijacking)
The IoT Endgame: SMB as a double-edged sword
The compromised webcam became a ransomware launchpad through three critical oversights:
- Unmonitored SMB Traffic
Attackers mounted writable network shares (\NAS01\Finance) from the webcam’s BusyBox environment using: bashmount -t cifs //NAS01/Finance /mnt/encrypt -o username=service_acct,password=P@ssw0rd123EDR solutions typically ignore SMB traffic from IoT devices, allowing 14TB of financial data encryption without alerts. - Linux Encryptor Advantages
Akira’s ELF-based ransomware (SHA-256: 9a327d3f…) exploited the webcam’s ARMv7 architecture, achieving 3.2× faster encryption speeds than their Windows variant. - Persistence Through Neglect
The webcam had 647 days of uptime—well beyond the 45-day IoT patch cycle recommended by CIS Benchmarks.
Lessons for cyberdefense teams
- IoT Risk Quantification
- Conduct asset fingerprinting using tools like runZero to identify all IP-connected devices
- Apply the NIST IR 8259A IoT security baseline to non-compute devices
- Network Microsegmentation
Implement Zero Trust Architecture (ZTA) policies isolating IoT devices: python# Sample Cisco ACI policy Tenant = "IoT_Segment" EPG = "Surveillance_Devices" Contract = "Block_SMB_Outbound" - EDR Augmentation Strategies
- Deploy network detection (NDR) tools monitoring SMB protocol anomalies
- Configure SIEM rules alerting on IoT devices initiating SMB writes
The path forward: beyond device class bias
This attack underscores a critical paradigm shift—IoT devices now possess sufficient compute power (many run on quad-core ARM processors) to execute complex attacks. Defense strategies must evolve to:
- Treat all IP-enabled devices as potential attack surfaces
- Extend vulnerability management to include IoT firmware (CISA’s SBOM mandate helps)
- Implement cross-domain detection rules (e.g., alert if a thermostat runs cryptolibraries)
Actionable recommendations
- Immediately audit all IoT devices for:
- Open SMB ports (445/TCP)
- Default credentials (use Shodan dork:
webcam x-pow ered-by: axis)
- Apply MITRE D3FEND Tactic D3-NTA-IE against IoT exploitation
- Conduct purple team exercises simulating IoT-based ransomware pivots
The Akira incident isn’t just about a webcam—it’s a harbinger of ransomware’s next evolution. As attackers weaponize everything from HVAC systems to smart elevators, defense must become as ubiquitous as connectivity itself.