In a cyber operation, the U.S. Department of Justice (DOJ) and the FBI have successfully removed the PlugX malware from over 4,200 computers across the United States. This malware, linked to the Chinese state-sponsored hacking group Mustang Panda (also known as Twill Typhoon), has been notorious for its use in cyber espionage and data theft since at least 2014.
The operation’s background
The DOJ’s initiative was authorized through a series of court orders obtained in August 2024, allowing law enforcement to conduct a remote deletion of the malware from infected systems. This operation was not only a domestic effort but also part of a broader international collaboration with French authorities and cybersecurity firm Sekoia.io, which played a crucial role in identifying and neutralizing the malware.
According to U.S. officials, PlugX is particularly insidious because it can maintain persistence on infected machines by creating registry keys that ensure it runs whenever the computer is started. The malware has been used to target a wide range of victims globally, including European shipping companies and various governments in the Indo-Pacific region.
Technical details of the malware
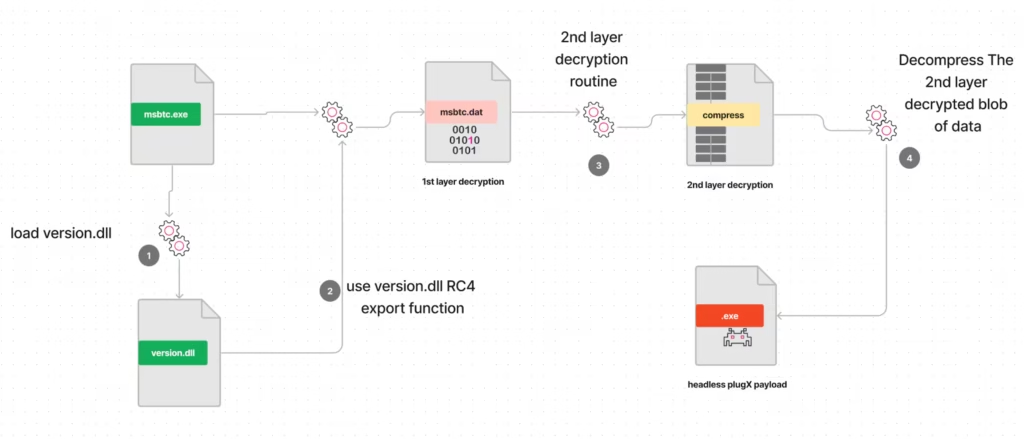
PlugX is classified as a Remote Access Trojan (RAT), enabling hackers to control infected computers remotely. Its capabilities include collecting sensitive information, uploading and downloading files, logging keystrokes, and executing commands on victim machines. The malware can spread through various means, including USB flash drives, making it a versatile tool for cybercriminals.The FBI’s approach to removing PlugX involved sending a command to the infected computers that executed several critical tasks:
- Deleting files created by PlugX on the victim’s computer.
- Removing registry keys used to ensure PlugX runs automatically.
- Stopping and deleting the PlugX application entirely from the system.
This meticulous process ensured that no legitimate functions of the computers were disrupted during the cleanup.
Implications and future outlook
The DOJ’s operation highlights a growing trend where law enforcement agencies are taking proactive measures against cyber threats by employing court-authorized counter-hacking techniques. U.S. Attorney Jacqueline Romero emphasized that this operation underscores the recklessness of state-sponsored hackers and demonstrates a commitment to protecting U.S. cybersecurity through collaborative efforts with international partners.
As cyber threats continue to evolve, this operation serves as a reminder of the ongoing battle against sophisticated malware like PlugX. With its extensive history and capabilities, it remains crucial for both private and public sectors to stay vigilant against such threats, ensuring robust cybersecurity measures are in place.
The DOJ has also committed to notifying affected computer owners through their internet service providers, marking an important step in transparency and accountability in cybersecurity operations.
While this operation marks a significant victory against one of the most pervasive pieces of malware linked to state-sponsored hacking, it also highlights the need for continuous vigilance in an increasingly complex cyber landscape.