Read Time:1 Minute, 43 Second
A botnet is a formidable network of compromised devices controlled by a central entity known as a bot herder. These devices, known as bots, are infected with malware and can be used to execute various malicious activities. Recently, the discovery of the Raptor Train botnet has raised alarm within the cybersecurity community.
Raptor Train Botnet
The Raptor Train botnet, attributed to the Flax Typhoon threat group, is a sophisticated Chinese state-sponsored network targeting over 200,000 SOHO routers, NVR/DVR devices, NAS servers, and IP cameras since 2020. It utilizes a custom Mirai variant called Nosedive as its primary implant.
Botnet Structure and Management
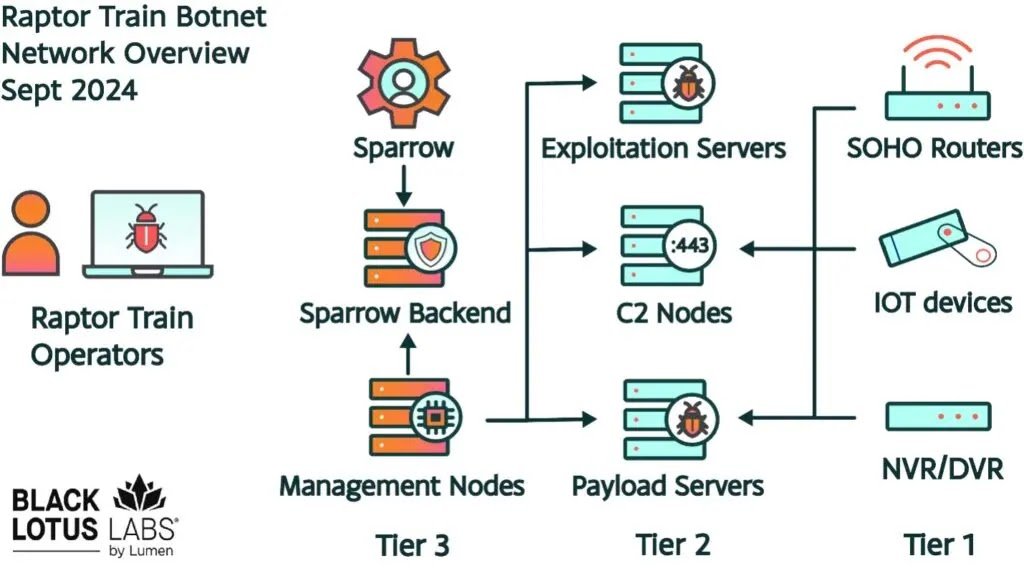
Raptor Train operates with a three-tier structure:
- Tier 1: Compromised devices
- Tier 2: Exploitation, payload, and command and control (C2) servers
- Tier 3: Management nodes
The botnet is managed through an advanced control system called Sparrow, which enables large-scale exploitation, vulnerability management, remote command execution, and potential distributed denial-of-service (DDoS) capabilities.
Targets and Evasion Techniques
Raptor Train primarily targets U.S. and Taiwanese entities in critical sectors like the military, government, education, and telecommunications. To evade detection, it employs various techniques such as memory-only execution and anti-forensics methods.
Campaign Evolution
The Raptor Train botnet has evolved through four campaigns: - Crossbill
- Finch
- Canary
- Oriole
Each campaign employed distinct tactics and targeted specific devices and vulnerabilities.
Mitigation Strategies
To mitigate the risks posed by the Raptor Train botnet, cybersecurity professionals recommend the following measures: - Network defenders should monitor for large data transfers, even locally.
- Organizations should adopt SASE (Secure Access Service Edge) solutions for enhanced security.
- SOHO users should reboot and update their routers regularly and consider using EDR (Endpoint Detection and Response) solutions.
- Users should replace end-of-life devices to reduce risks.
Conclusion
The Raptor Train botnet is a significant threat with far-reaching implications for cybersecurity. By understanding its structure, tactics, and evasion techniques, organizations and individuals can implement effective mitigation strategies to safeguard their systems and data. Continuous monitoring, advanced security solutions, and proactive patching are essential for maintaining a robust defense against such sophisticated cyber threats.